BitRaser File Eraser

4.5. Set Preferences for BitRaser File Eraser
BitRaser File Eraser gives you options to change erasure settings as per requirement.
To apply the preferences :
1. Run BitRaser File Eraser.
2. This section explains how to set preferences as per requirements. In the preferences list there are two options:
-
Settings.
-
Update.
To set the setting preferences follow the steps below:
a) From the drop-down, select Settings  option. The dialog box displays:
option. The dialog box displays:
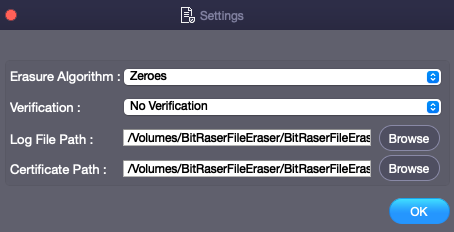
The Settings dialog box consists of the following fields:
-
Erasure Algorithm : Select the desired algorithm from the list of provided algorithms. Refer List of Erasure Algorithms and their Descriptions for details.
-
Verification : Select the desired verification method to verify the data deletion from the respective location.
-
No Verification : No verification is done after the traces are erased.
-
Random Verification : Random verification of the storage device is done after the erasing operation, that is, randomly selected sectors of the storage device are verified after erasing operation.
-
Total Verification : Total verification verifies all the sectors of the storage device after the erasing operation is completed.
-
-
Log File Path : Select the location for saving the Log File generated during the erasure process by clicking on Browse button.
-
Certificate Path : Select the location for saving the certificate by clicking on Browse button.
Click OK to apply the settings.
b) From the drop-down, select Update. Refer Updating the Software.
List of Erasure Algorithms and their Descriptions:
| Sr. No. | List of Algorithms | Number of Passes |
Description |
| 1 | Zeroes | 1 | It is the fastest algorithm. It erases all data by overwriting zeroes in a single pass. |
| 2 | Pseudo-random | 1 | This algorithm overwrites entire hard drive with randomly generated numbers in a single pass. |
| 3 | Pseudo-random & Zeroes | 2 | It overwrites hard drive in two passes. First pass overwrites data with randomly generated numbers and second pass overwrites data with zeroes. |
|
4 |
Random Random Zero |
6 | This algorithm erases data by overwriting a storage media with random characters in multiple passes. |
| 5 | DoD 5220.22 - M | 3 | This algorithm is specified by U.S. Department of Defense. It overwrites hard drive in three passes. First pass overwrites data with zeroes, second pass overwrites data with ones and third pass overwrites data with randomly generated bytes. |
| 6 | DoD 5200.28 - STD | 7 | This algorithm is specified by U.S. Department of Defense. It overwrites hard drive in seven passes. First two passes overwrite data with certain bytes and their complements. Next two passes overwrite data with random characters. Fifth and sixth passes overwrite data with a character and its complements. Final pass overwrites data with random characters. |
| 7 | DoD 5200.22-M (ECE) | 7 | This algorithm erases data by overwriting the hard drive in seven passes. The first, fourth and fifth pass is overwriting with a random byte, its 8 right-bit shift complement and 16 right-bit shift complement; second and sixth passes are overwriting with zeroes, and third and seventh pass with random data. |
| 8 | Russian Standard - GOST R-50739-95 |
2 |
It overwrites hard disk with zeroes followed by a single pass of random characters. |
| 9 | B.Schneier's algorithm | 7 | The Bruce Schneier algorithm has seven passes. First two passes overwrite hard disk with ones and zeroes respectively and the next five passes overwrite data with random characters. |
| 10 | German Standard, VSITR | 7 | The German Standard erasing algorithm overwrites data with three alternating patterns of zeroes and ones and the last pass overwrites data with random characters. |
| 11 | Peter Gutmann | 35 |
This algorithm overwrites data 35 times making recovery of data by any tool impossible. This algorithm takes more time than other algorithms. |
| 12 | US Army AR 380-19 | 3 | This algorithm is specified by U.S. Army. This is a three pass algorithm. First pass overwrites data with random bytes. Second and third pass overwrite data with certain bytes and their complements respectively. |
| 13 | North Atlantic Treaty Organization - NATO Standard | 7 | This is a seven pass algorithm. From pass one to six, it overwrites data with a number and its complement alternatively. Pass seven overwrites data with random characters. |
| 14 | US Air Force, AFSSI 5020 | 3 | It overwrites data in three passes. First with zeroes, then with ones and then with random characters. |
| 15 | Pfitzner Algorithm | 33 | The Pfitzner algorithm is a used in file shredding and data destruction programs to overwrite existing information on a hard drive or other storage device. All the passes in Pfitzner method consists entirely of random overwriting of data in the storage device. |
| 16 | Canadian RCMP TSSIT OPS-II | 4 |
This algorithm is a four pass overwriting algorithm with alternating patterns of zeroes and ones and the last pass - with a random byte. |
| 17 | British HMG IS5 | 3 | This algorithm is a three pass overwriting algorithm, first pass - with zeroes, second pass – with ones and the last pass with random data. |
| 18 | NIST 800-88 Purge | 1 | Apply the ATA Secure Erase command. The sanitize command is preferred to Secure Erase when the sanitize command is supported by the device. |
 3. Getting Started
3. Getting Started