Stellar Eraser for Mobile

4.2. Erasure Process
You can securely erase data from your device by using the erasure feature of Stellar Eraser for Mobile. You can choose an erasure method from a list of 11 data erasure methods.
To erase data using Stellar Eraser for Mobile:
1. Run Stellar Eraser for Mobile. Plug the iOS/Android device into the computer.
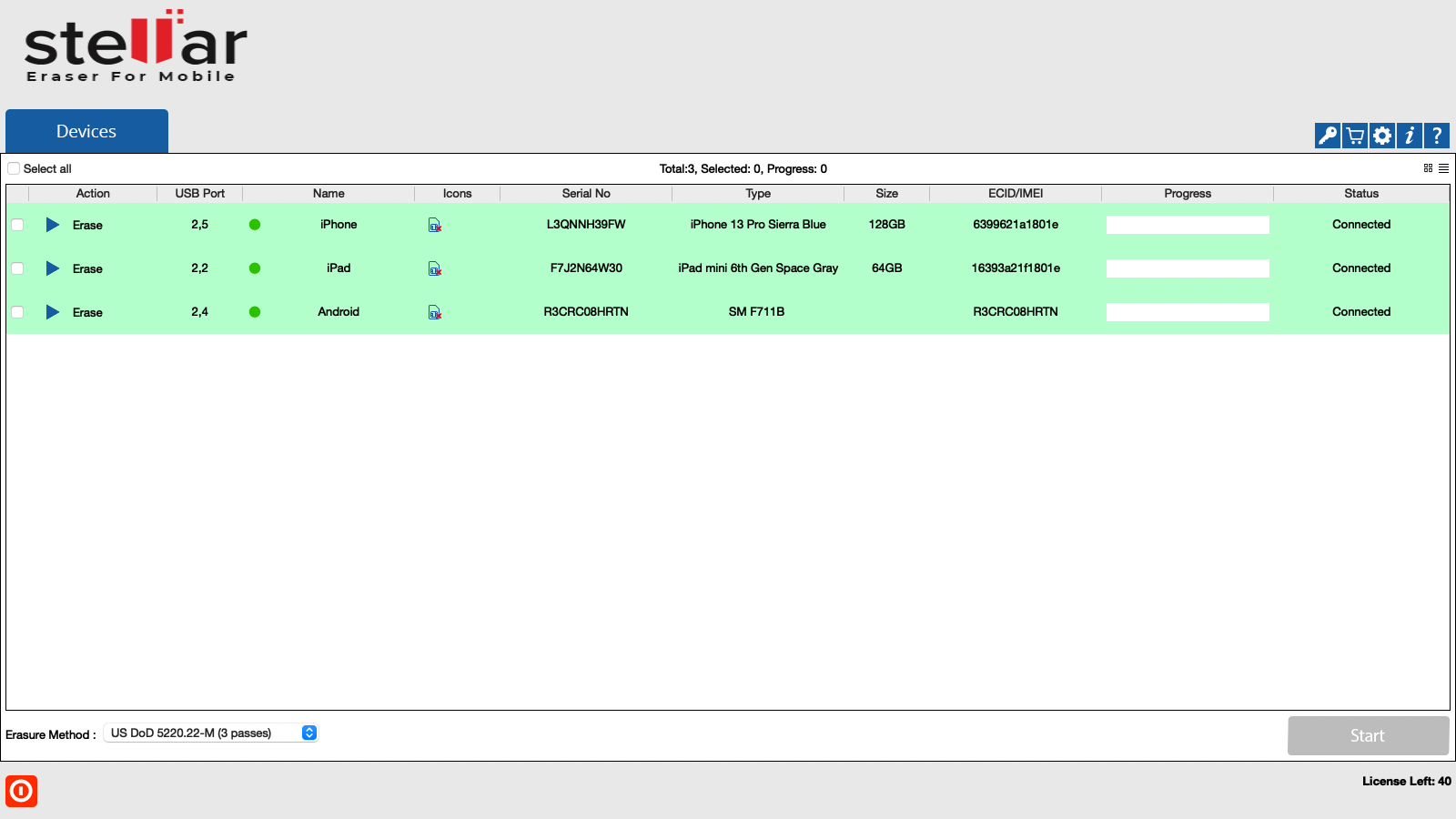
2. The Devices tab lists all the attached iOS/Android devices. The screen which appears is displayed below:
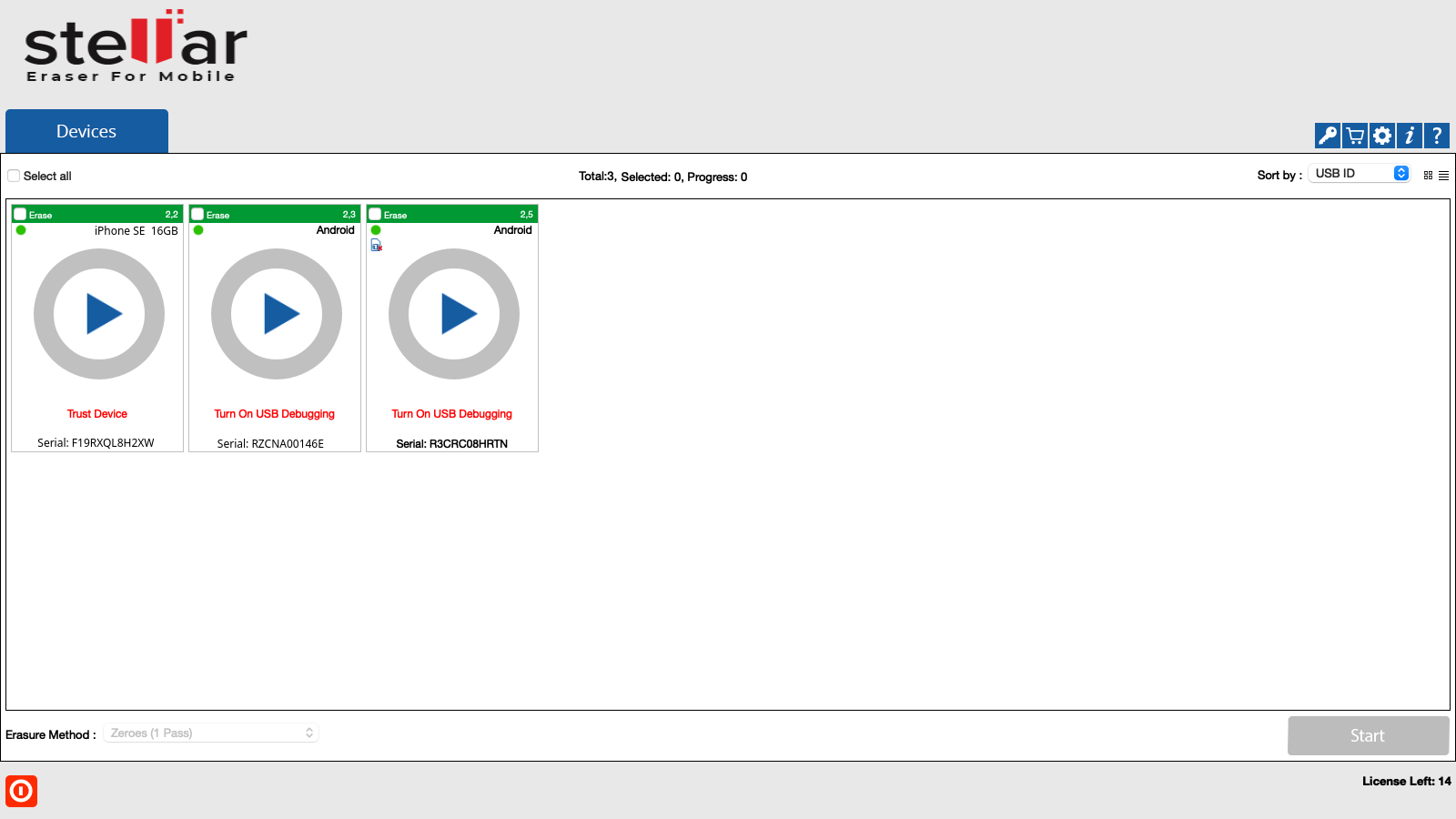
A device message appears after its connection. For example: In the above screen, an Android device shows the message 'Turn On USB Debugging'. To continue from this stage, USB Debugging must be allowed on the Android device's end. Similarly, for iOS devices 'Trust Device' message appears.
Note: For more information, please refer to the section 'How to enable the USB Debugging mode in your phone?' in the next topic of this user guide.
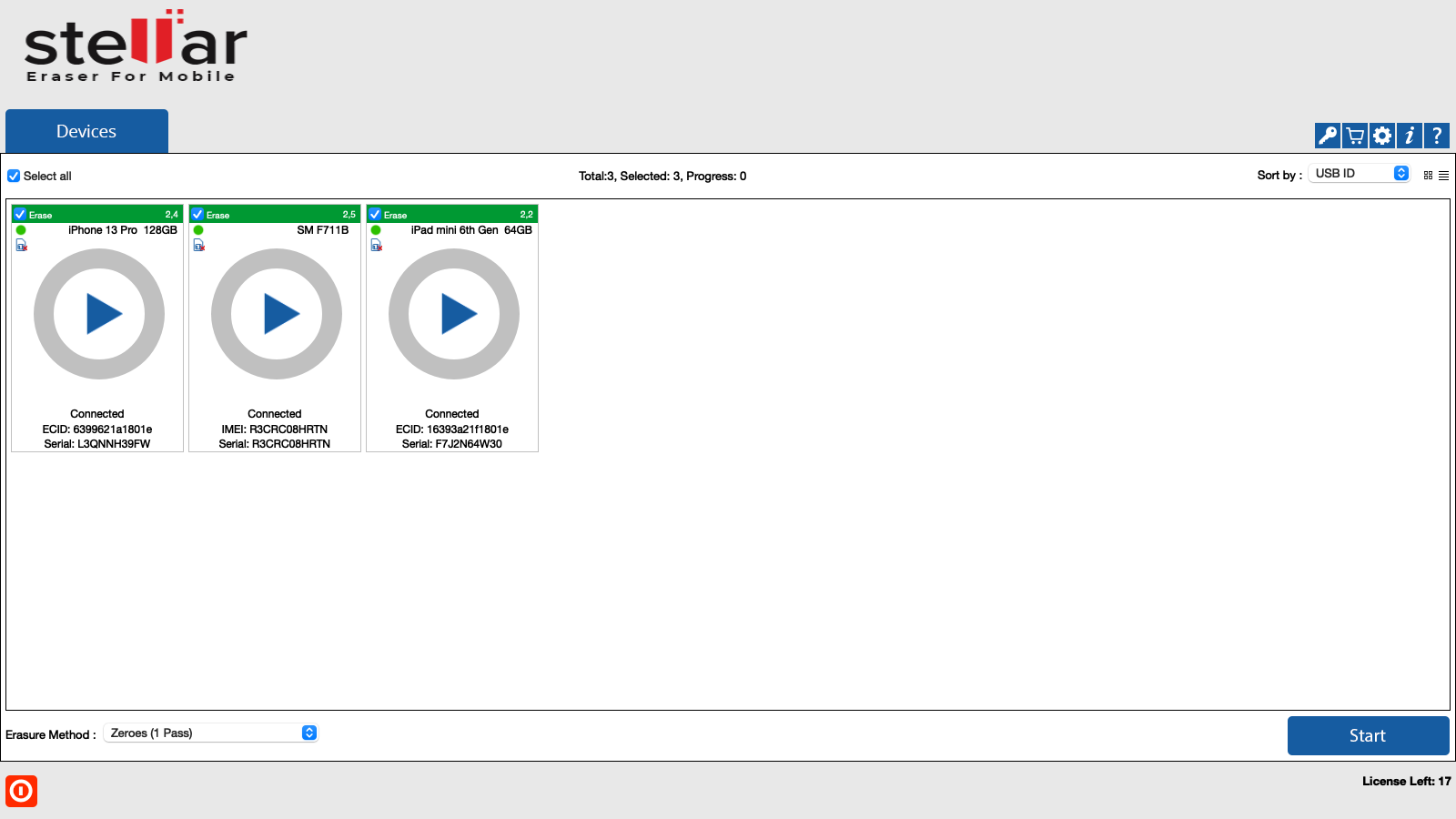
3. All the devices along with their information like process (Erase), USB port name, type, progress bar, status, ECID/IMEI, and serial number are displayed. You can also see icons for connectivity status, SIM card status, and FMD (Find my device) locked/unlocked status.
4. You can preview the device's information either in Grid view  or List view
or List view  .
.
- In the Grid view, the devices get displayed in a grid-like structure, and also the devices can be sort using the Sort By option. The Sort By option allows sorting the devices based on the following information/criteria: USB ID, Name, Serial Number, Type, Size, ECID/IMEI, and Status.
.png)
- In the List view, the devices get displayed in a list.
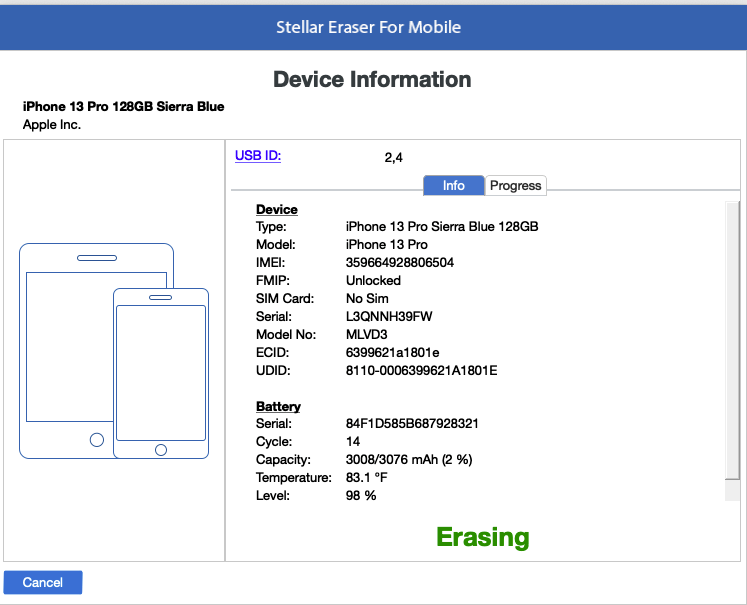
5. Double-clicking on any of the displayed devices will show the device information of the corresponding device.
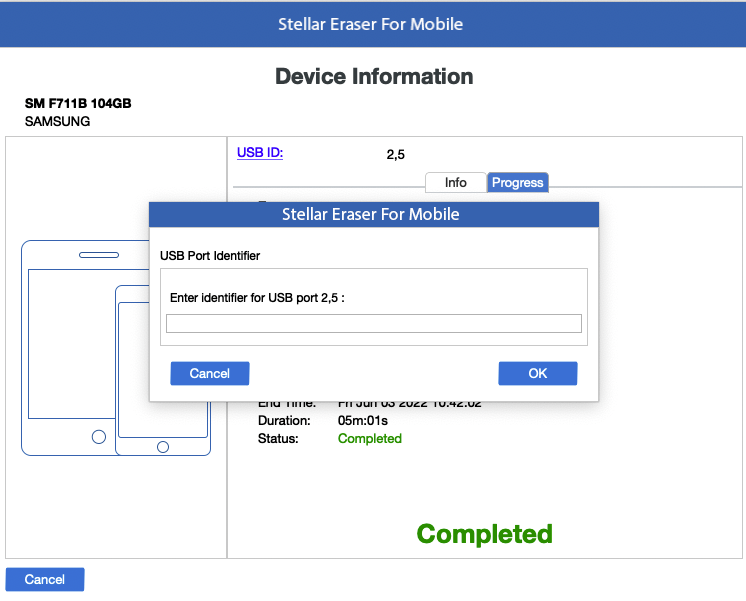
6. From the dialog that appears, click on USB ID to change the identifier for the USB port. A dailog box opens, enter the USB Port Identifire name in the text field and click OK.
7. Select the devices to erase by marking the check-box before every device.
Note: Mark Select All option to select every listed device for erasing.
8. From the bottom of the screen, select any one of the following erasure methods:
|
Erasure Methods |
Description |
|
NIST 800-88 Purge |
This algorithm wipes data by overwriting the HDD or SSD drives using the Cryptographic Erase (CE) of a Self-Encrypting Drive (SED). |
|
Native OS Erasure |
This is the default algorithm available to the users in the device's OS. |
|
Zeroes |
This algorithm wipes data by overwriting it with zeros in a single pass. This is the fastest algorithm available to a user. |
|
Pseudo-random (1 Pass) |
This algorithm wipes data by overwriting an entire device with randomly generated numbers in a single pass. |
|
US Department of Defense, DoD 5220.22-M (3 passes) |
This algorithm wipes data by overwriting the device in three passes. In the first pass, it overwrites data with zeros, then in the second pass, it overwrites the data with ones, and finally in the third pass overwrites the data with randomly generated bytes. This is a U.S. Department of Defense algorithm. |
|
US Department of Defense, DoD 5200.22-M (ECE) (7 passes) |
This algorithm wipes data by overwriting the device in seven passes. The first, fourth, and fifth pass are overwriting with a random byte, its 8 right-bit shift complement, and 16 right-bit shift complement; second and sixth passes are overwriting with zeros, and third and seventh pass with random data. This is a U.S. Department of Defense algorithm. |
|
B.Schneier's algorithm (7 passes) |
This algorithm wipes data in seven passes. In the first two passes, it overwrites the device with ones and then zeros, and in the next five passes, it overwrites data with random characters. |
|
Peter Gutmann (35 passes) |
This algorithm wipes data by overwriting it 35 times, making recovery of the wiped data by any tool impossible. This algorithm takes more time than other wiping algorithms. |
|
US-Army AR 380-19 (3 passes) |
This algorithm wipes data by overwriting the media in three passes. In the first pass, it overwrites data with random bytes, then in the second and third pass, it overwrites data with certain bytes and their complements. This is a U.S. Army algorithm. |
|
US Air Force, AFSSI 5020(3 passes) |
This algorithm wipes data by overwriting the media in three passes. First, it overwrites with zeros, then with ones, and finally with random characters. |
|
British HMG IS5 (3 passes) |
This algorithm is a three pass overwriting algorithm, first pass - with zeros, the second pass–with ones and the last pass with random data. |
9. Click Start to start erasing the devices.
Note: If you wish to erase a single device, you can start the process by simply clicking the play button in the middle.
10. A warning message appears asking to proceed to the erasure process. Click Proceed.

Note: If you do not wish to see the warning message the next time you erase a device, select the Don't Show Again check-box.
The erase process for a device takes place in five different phases, to understand these phases refer to the next section of Erasure Stages.
 3. Getting Started
3. Getting Started