Microsoft recently detected multiple zero-day vulnerabilities on on-premises versions of the Exchange server. According to Microsoft Threat Intelligence Center, these vulnerabilities are exploited by the Hafnium group – an attack group believed to be backed by China. The threat actors primarily target businesses and institutions in the United States, using US-based Virtual Private Servers (VPS), to get remote access to Exchange servers for stealing critical data from the organization’s network.
As per reports, the Hafnium group has hacked over 30,000 organizations in a few days till March 05. As of March 12, Microsoft has estimated that more than 82,000 Exchange servers (from an initial 400,000 on March 01) are still vulnerable globally.
In response to the Hafnium attack, Microsoft has released multiple security updates for the Exchange server. It is highly recommended to update the on-premises Exchange server immediately.
How Hafnium Works?
Hafnium exploits vulnerabilities on unpatched systems and takes advantage of Exchange authentication architecture to access on-premises Exchange server with administrative privileges and deploy web shells on the victim’s server.
These web shells potentially enable threat actors to access the email accounts and facilitate the installation of additional malware or ransomware on the victim’s environment to compromise the system further. The vulnerabilities being exploited are CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065.
How to Mitigate the Risks and Recover Exchange Server after Hafnium Attack?
You can take the following actions to mitigate the risks and recover user mailboxes from the affected Exchange server.
Microsoft has released Exchange On-Premises Mitigation Tool (EOMT) that works with MS Exchange 2019, 2016, and 2013. It will also work on Exchange 2010 with PowerShell 3.0 support but has minimum functionality.
The tool addresses CVE-2021-26855 vulnerability. The tool helps you check if your Exchange server is vulnerable. To use EOMT, follow these steps:
- Download the EOMT tool and extract the Security folder at your desired location.
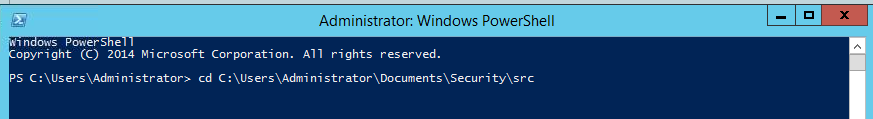
- Open PowerShell as administrator and then navigate to the extracted folder location. In our case, it is:
cd C:\Users\Administrator\Documents\Security\src
- Now run the EOMT.ps1 script to check if your server is vulnerable.
.\EOMT.ps1
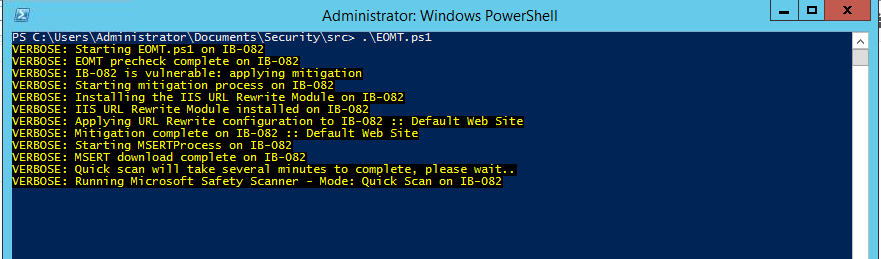
The script checks if the server is vulnerable by downloading and installing the IIS URL rewrite tool. It then downloads and runs Microsoft Safety Scanner or MSERT in quick scan mode. The MSERT scans and removes threats and web shells from the server.
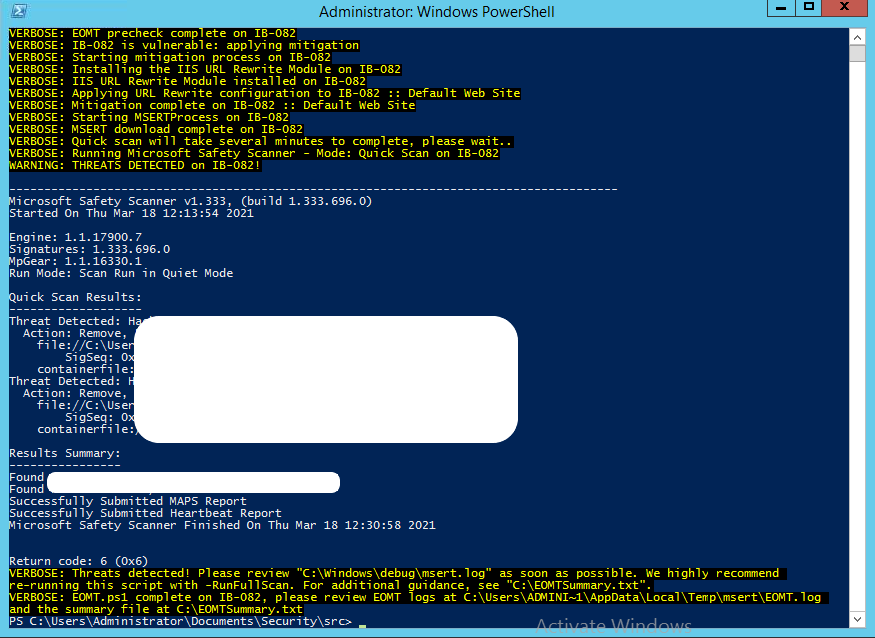
If the server isn’t vulnerable, it only runs the MSERT quick scan.
You may also run Text-ProxyLogon.ps1 (formerly known as Test-Hafnium) to automate the commands. It runs CVE-2021-26855 test much faster and exports the report in CSV files. The CSV file contains list of suspicious zip/rar/7x files that script finds in Program Data. Web shells are known to use such file formats for exfiltration.
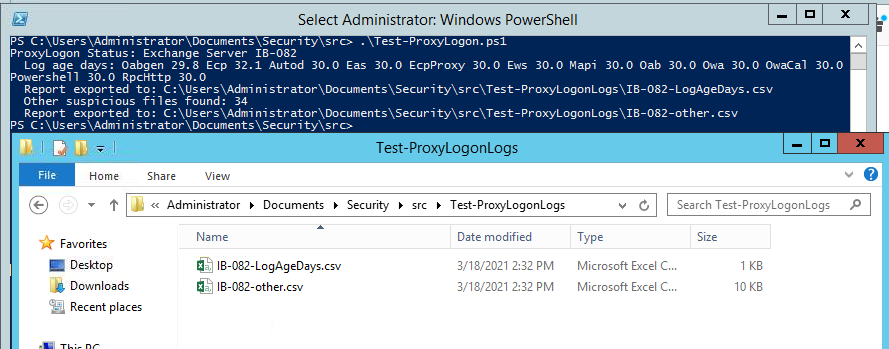
Review each file to check if these files are valid.
2. Update Affected Exchange Servers
Exchange 2007 and 2003 are believed to be unaffected from the Hafnium attack. However, you must upgrade the server to a supported version to continue getting updates.
Exchange 2010 is impacted by CVE-2021-26857 vulnerability only. Update the server with latest security patches and use EOMT script to investigate the server for possible exploitation.
Exchange 2019, 2016, and 2013 are the most impacted Exchange server versions. You must apply mitigation steps discussed above and install March 2021 Exchange Server Security Updates.
3. Restore from Backup
If your Exchange server is compromised and broken or crashed due to the Hafnium attack, you can use Setup /m:recoverserver to recover the server. However, it is critical to keep the Windows Server and Exchange version the same on the new server to avoid issues.
Then use your backup to restore the database on a new server and shut down or delete the infected one.
Exchange server recovery tool, such as Stellar Repair for Exchange, comes in handy when you do not have a backup. The software helps administrators recover Exchange server from malicious attacks. It also helps repair damaged databases due to server crashes, power failure, or hacking and can greatly reduce downtime scenarios.
The software lets you extract mailboxes from a compromised Exchange server database and saves them into PST. You may also export the mailboxes from the database directly to a live Exchange server or Office 365. It works with MS Exchange 2019 and older versions, including Exchange 5.5.
NOTE: Run EOMT script before using Stellar Repair for Exchange software.
To Wrap up
Hafnium is not new. It has previously attacked entities in the US across various industries. Thus, it is important to learn techniques to protect unpatched servers from such attacks. By enabling effective defense and backup techniques, you can safeguard your Exchange servers from future attacks.
Was this article helpful?