When you hand over your computer to a service provider for repair, you automatically assume that your data will remain secure. Most of us would not even think twice about the possibility of potential tampering with our devices. But nothing could be further from the truth.
A study conducted by researchers at the University of Guelph in Ontario, Canada, revealed shocking outcomes. The researchers found that technicians snooped on and copied personal data from devices, particularly those belonging to female customers.
In multiple instances, revealing photos were saved to an external device, and password-containing files were duplicated. Some workers even attempted to cover their tracks by removing evidence or not generating it at all. Does this make you feel worried? Well, it should.
The most important lesson a user can learn from this is that without proper measures, your sensitive information can be easily compromised. Especially, if you’re handing over your device to a third-party (think repair shops) entity with administrative access to the device’s operating system for installation, diagnostics, or validation.
How Vulnerable is Your Data When You Send Your Laptop for Repair?
Taking your laptop to a technician without prior safeguards can put your data at risk. While most repair & service providers may be ethical and respect customer privacy, few have proper privacy policies in place. Therefore, it’s crucial to be aware of the threats to your privacy when your device is not in your possession. Here’s are some of the potential risks:
Direct Access: In some cases, the technician might need to gain passwords or administrative privileges to access your computer, diagnose the issues, and repair it. This gives them direct access to your private data.
Remote Access: If a technician offers remote support, they could use remote access tools to take control of your system. It can allow them to access and transfer your sensitive files or data
Hard Drive Cloning: Repair procedures often require cloning your hard drive to back up the data before making modifications to your computer. This allows the technician to keep a copy of all your data.
Installing Malware: With easy access to your device, they can install spyware or Remote Access Trojan (RAT) to monitor your activity or gain remote access to your device.
Bypassing Passwords and Encryption: Advanced technicians could even use tools and techniques to crack your passwords and bypass weak encryption on your hard drive.
Signs and Symptoms of a Compromised Device
Apart from directly stealing your data, a repair technician with bad intentions can go a step further and gain unauthorized access to your device by installing viruses or malware on it. Here are some common warning signs that your computer might have been hacked or compromised, exposing your sensitive data:
Antivirus Warnings: Frequent alerts from your antivirus, detecting malicious software on your system, suggest that something is wrong. Further, if strange messages pop up saying your antivirus has been disabled, it’s possible that an attacker has gained unauthorized access to your computer.
Webcam Light: If your webcam’s light mysteriously gets on and off, a hacker may use a Remote Access Trojan (RAT) or some other malware to spy on you.
Unusually Slow Performance: Presence of a malicious software, such as crypto-mining malware, can exhaust system resources and slow down your computer’s performance.
System Freezes and App Crashes: If your operating system keeps freezing and apps frequently crash, it’s a sign that something is not quite right.
Browser and Password Changes: Modifications to your browser’s homepage, extensions, or passwords changes mean your system has been compromised.
Practical Tips to Safeguard Your Data Before Giving Your Laptop for Repair
Most repair shops do not have stringent customer data and privacy protection policies in place, making it easy for technicians to access your private data. This puts the onus on customers to take active steps and safeguard their personal data. Here’s what you can do:
Document the Current State of Your Device
The first thing to do is keep full track of the system’s current state, including existing issues, installed software, and the condition of your hardware. It will help you track signs of any suspicious changes or damages that occur during the repair procedure.
Firstly, keep your system updated to ensure the latest security layers are installed and make sure you have an antivirus program installed on your computer. Secondly, use strong passwords and back up all your important data to an external drive. Additionally, consider using security software that can track access to your device.
Choose a Reputable Shop for Servicing and Repair
Before taking your device for repair, always research well and look for reviews and ratings to find trustworthy businesses. A reputable service provider will handle your device with care and is less likely to cause any harm to your data and privacy.
Many websites like Yelp, Google reviews, and Better Business Bureau offer insights into the shop’s reputation. Additionally, you can verify if the technicians are certified by recognized organizations like CompTIA or Microsoft.
Communicate Your Concerns to the Service Provider
Clear communication with the service provider ensures they are on the same page as you, understand your privacy concerns, and take the right measures to protect your data. Enquire the shop about their data protection policies and how they handle a customer’s data.
You can go one step further and request a written statement from the service provider stating their commitment to protecting your privacy and specifying the parts of your device that a technician is allowed to access.
Use Encryption
Encrypting your hard drive converts your data into a code that can only be accessed using a password. It is hands-down one of the best approaches to prevent unauthorized access to your data. Even if someone removes your physical drive, they cannot read your files.
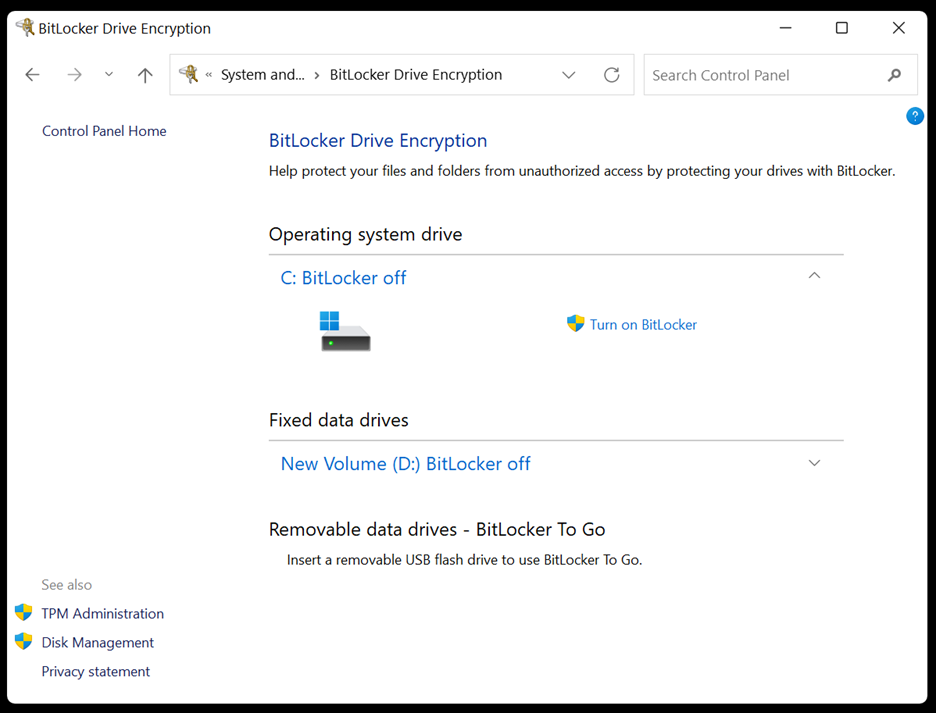
Windows users can use BitLocker to encrypt their files and folders. Simply go to Control Panel > System and Security > BitLocker Drive Encryption. Select the drives you want to encrypt and click Turn on BitLocker. Create a strong password and follow the on-screen prompts to complete the process.
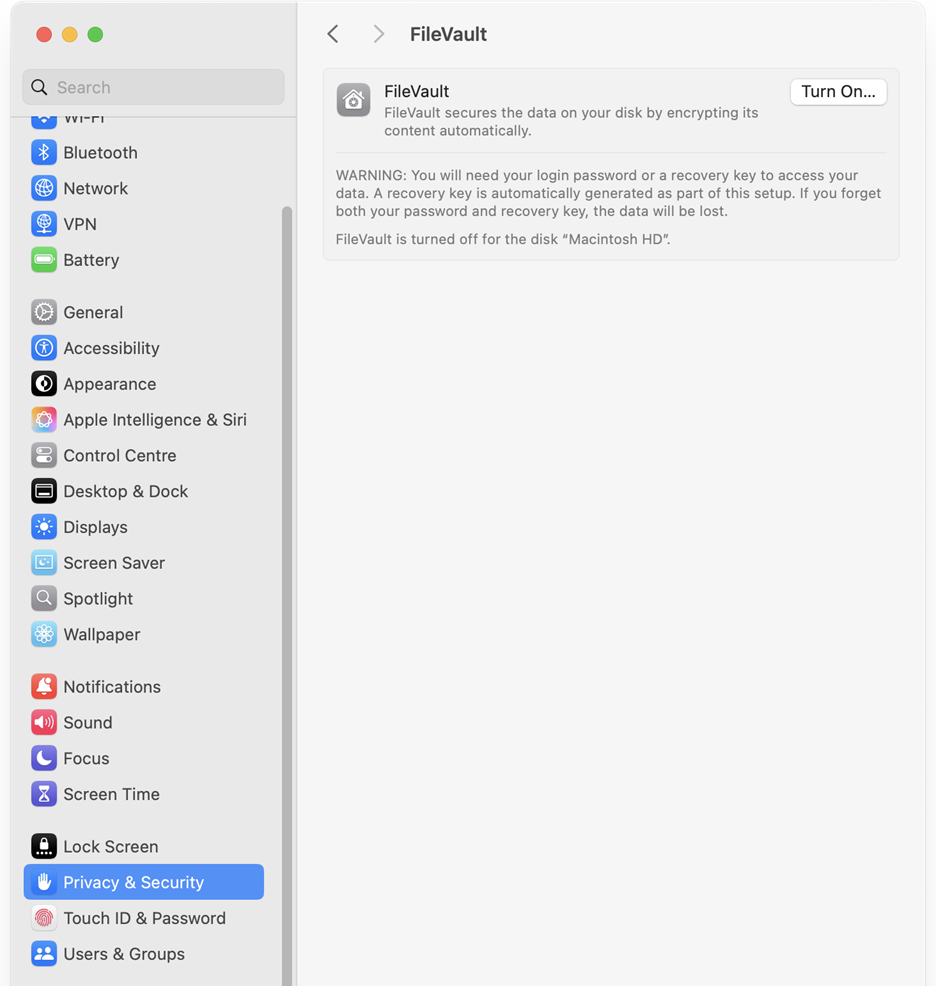
Alternatively, Mac users can use FileVault, a built-in utility within macOS, to encrypt their drives. For this, go to System Preferences > Privacy & Security > FileVault. Next, click on Turn on FileVault and follow the instructions to encrypt your files.
Erase Sensitive Data from Your PC
While hardware repair might seem less risky, your system can still be at risk. This is because the technician will ultimately need to access your laptop to check if the hardware is functioning properly.
The risk is even higher for software issues, as repairing them requires direct access to your hard drive, which contains all your documents, personal files, and browsing history. To circumvent this, backup your important data on an external drive and use a file eraser software to completely erase all the sensitive information on your system.
Note: Simply deleting the files and folders containing your sensitive data is not enough; as it can still be recovered using a professional-grade data recovery software.
Stellar File Eraser is a powerful DIY tool designed to erase files permanently, ensuring your sensitive data is securely erased from your device/laptop beyond the scope of any recovery. It securely erases internet activity, including cookies, favorites, search & browsing history across different web browsers. You can use it to remove temporary files, and application traces like activity log, preferences, and other personal information.
Follow the steps below to permanently erase files using Stellar File Eraser:
Step 1: Launch Stellar File Eraser on your PC.
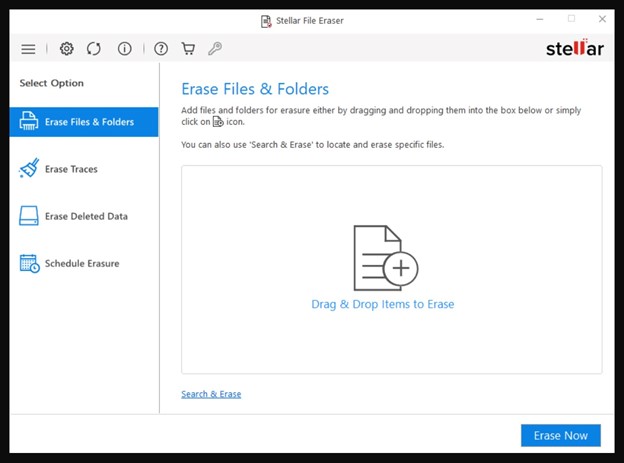
Step 2: Click on Erase Files & Folders in the left pane.
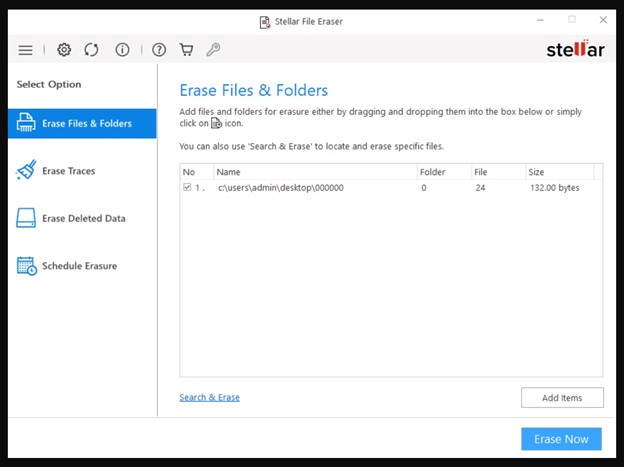
Step 3: Click Add Items to add the files you want to delete permanently and click Erase Now.
Step 4: A Confirm Erasure dialog box appears, click Proceed to continue.
Step 5: Process Completed window appears with the Erasure Summary of deleted files. Click OK to finish the process.
Bottom Line
Safeguarding your data while handing over your computer for repair requires proactive steps. By going for reputable service providers, using strong encryption, and securely erasing sensitive data, you can minimize the risk of data theft and protect your personal information. Remember to stay vigilant and take control of your privacy.
Was this article helpful?