Summary: Ransomware attacks, malware infections, man-in-the-middle attacks, etc., are some of the common cyber threats faced by organizations today. However, the most prevalent and dangerous cyber threat is phishing. Unfortunately, due to a lack of knowledge about email phishing, most people fall victim to such scams. According to a Verizon report, phishing accounts for 32% of all cyberattacks. In this blog, we take a closer look at email phishing and discuss some tell tale signs (with examples) that can help you identify a phishing email quickly.
What is Email Phishing?
Email phishing is a social engineering attack in which a cybercriminal uses a disguised email to steal login credentials, business documents, trade secrets, etc., from a recipient or a group of recipients. The sender masquerades as a trusted entity, like a government agency or a known organization, to trick the recipient into sharing sensitive information.

However, you can quickly identify phishing emails and protect yourself by being careful. The following are some tell tale signs that can help you spot a phishing email:
1. Message Received from Public Email Domain
Almost every reputed organization has its email domain and company account. So, if you have received an email from IRS whose website name is www.irs.gov, the email address should be contact@irs.gov or support@irs.gov (both end with “@irs.gov”). Generally, a reputed organization doesn’t send messages from a public email domain. If you receive an email from a reputed company or organization, but the email address has a public email domain, i.e., it ends with @gmail.com, @outlook.com, etc., then it can be a sign of a phishing attack.
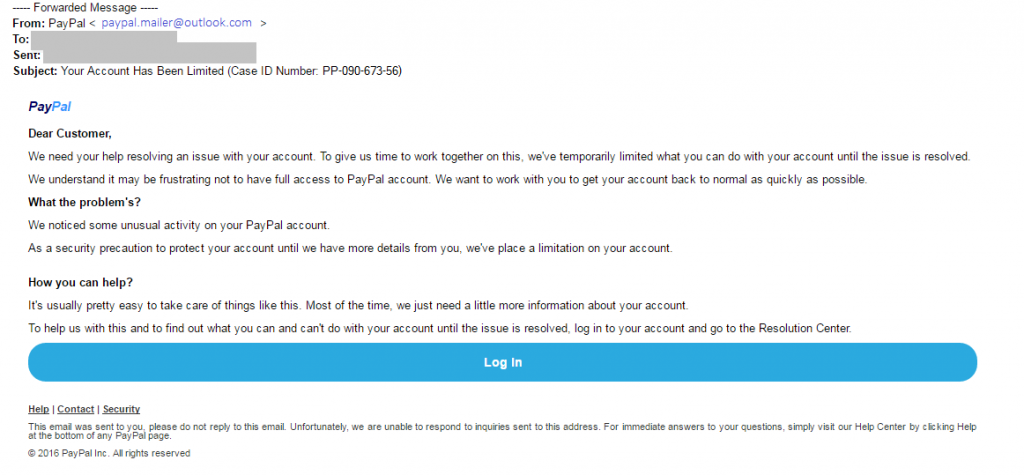 Figure 1: A Phishing Email Impersonating PayPal
Figure 1: A Phishing Email Impersonating PayPalFigure 1 illustrates a phishing email in which paypal.mailer@outlook.com sends the message. Note how the sender uses PayPal in the username to make it look legitimate. The sender even applied PayPal’s branding in the email content with the official logo and blue login button (blue is the primary color in PayPal’s branding) to trick the message receiver. However, the domain name @outlook.com is a dead giveaway. An official PayPal email will always have an email address that ends with @paypal.com.
2. Misspelled Domain Names
Some cybercriminals buy domain names similar to trusted ones to make the deceiving easier. For instance, they may buy a domain name, like www.linked-in.com or www.linkeden.com. Both domain names are similar to LinkedIn’s official domain name www.linkedin.com. They can then send an email from an address that looks like support@linked-in.com to mislead the recipient. Henceforth, you should always check the spelling of the email address when you receive a suspicious message before you respond.
3. Malicious Web Pages
Sometimes, cybercriminals send emails containing legitimate-looking URLs that trick the user into sharing personal, confidential, and financial information. When you click such a malicious URL, it usually takes you to a landing page, where you are asked to provide some sensitive information. This landing page can also give you signals about the phishing attack. You can refer to the sample landing page in Figure 2.
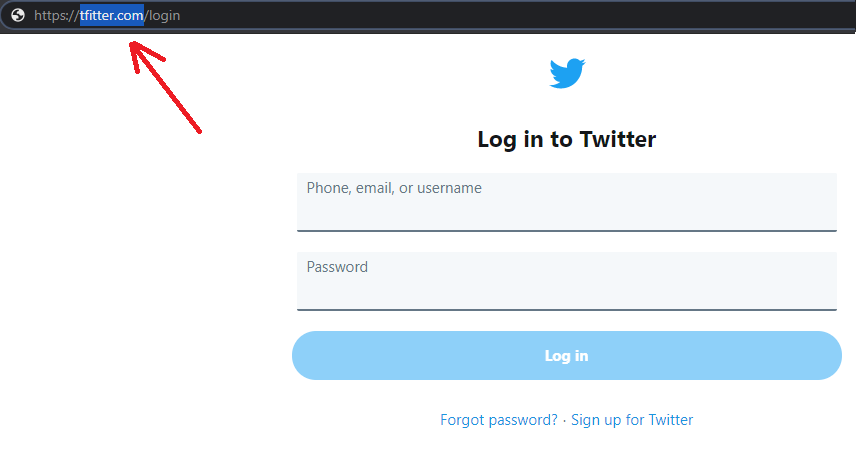 Figure 2: A Landing Page with Fake Twitter URL
Figure 2: A Landing Page with Fake Twitter URLThe following are a few signs that suggest it is a malicious web page:
- The web address is different from the official domain address of the company. At first glance, it looks like the login page of Twitter, but if you take a closer look at the URL, you can see that the domain name is http://tfitter.com and not http://twitter.com.
- Since the primary goal of malicious pages is to collect sensitive data, like login credentials, they often lack visual details like footers and headers (refer to Figure 3). Cybercriminals don’t always bother about making a landing page aesthetically pleasant or believable. There may be typographical and grammatical mistakes in the content that a victim won’t usually expect on the websites of reputed companies.
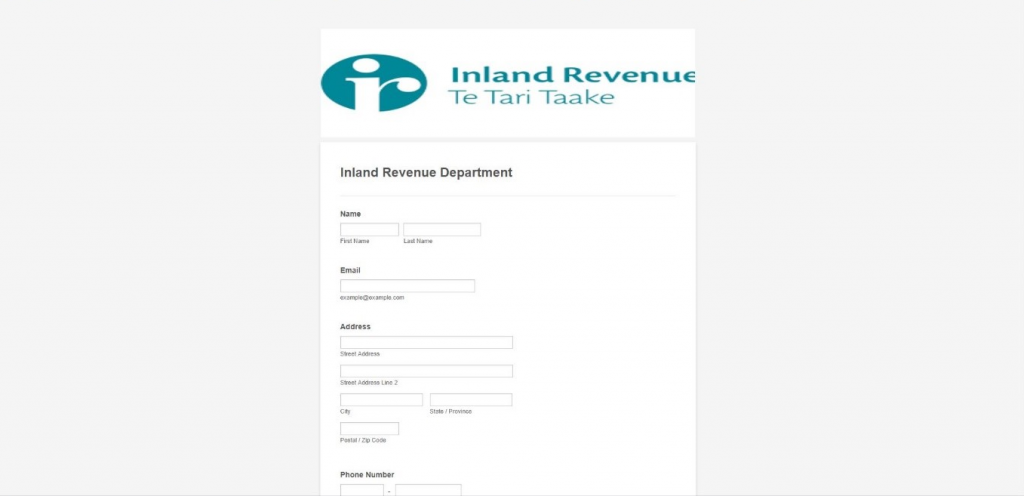 Figure 3: A Landing Page with no Visual Details
Figure 3: A Landing Page with no Visual DetailsLinkedIn messages and emails are also used by cybercriminals to launch phishing attacks. Refer to Figure 4, where a LinkedIn user has received an email from a threat actor who has disguised himself as a Wells Fargo representative.
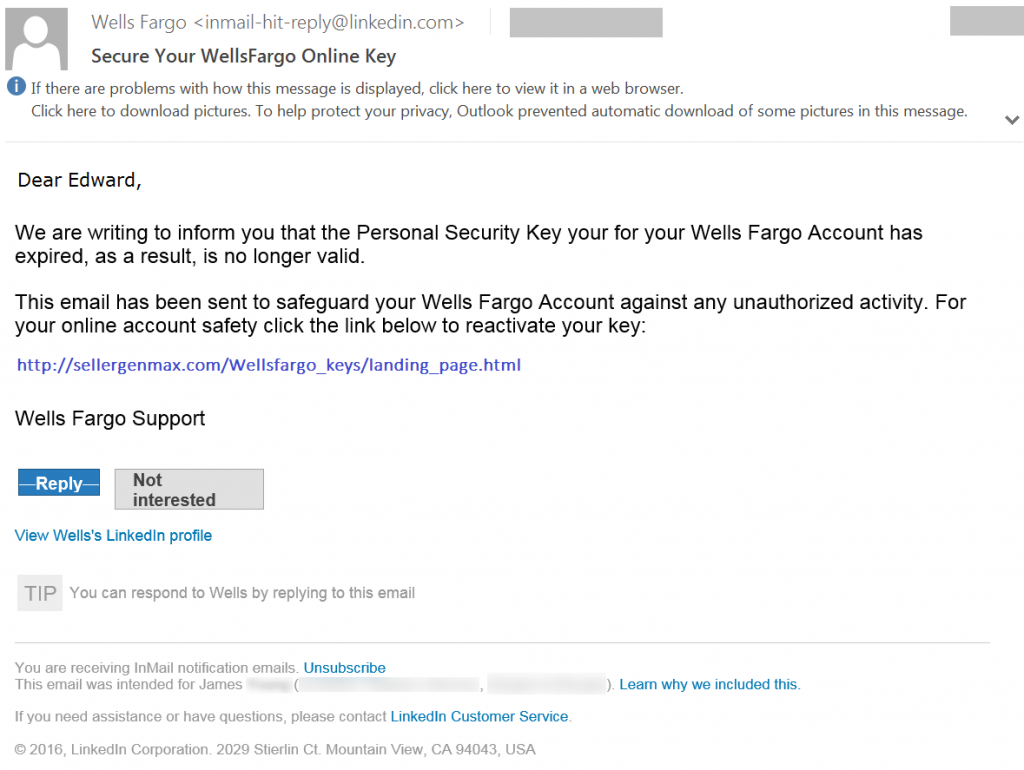 Figure 4: A Phishing Email Sent Via LinkedIn
Figure 4: A Phishing Email Sent Via LinkedInIn this example, the attacker has created a fake Wells Fargo account to send a phishing message through LinkedIn’s InMail. The message appears genuine, even though it contains a malicious URL, as LinkedIn itself delivers it. As you can see, no suspicious email addresses or domain names can be seen here. Also, the footer links for “Reply” and “Not Interested” buttons, etc., are generated by LinkedIn itself. These details make the message look authentic and make it easier for the hacker to scam the receiver.
To verify such kind of phishing attack, you can check the LinkedIn profile of the sender. The following are some common signs of a fake account:
- Beware of incomplete profiles that lack basic details, like experience, summary, recommendations, etc. Fraudsters usually don’t bother to fill in such details.
- The profile image may be irrelevant or would be of poor quality.
- There may be limited connections.
- Spelling errors or the use of poor grammar in profile details.
- Few or no interactions with other users.
Conclusion
Phishing emails are dangerous on many levels for an organization or business. For example, it takes just one unaware employee to click a malicious URL to initiate a malware attack that may infect all the company servers or compromise the company’s account, resulting in a massive data breach. So, all your company’s incoming and outgoing emails must be monitored for anomalies, malicious links, and details. Also, it is vital to provide cyber hygiene training and conduct awareness programs to inform the employees about email phishing attacks and how they can spot such phishing emails.
Suppose you have encountered an email phishing attack in your company and want the forensic analysis of emails. In that case, a specialized eDiscovery software for email investigation like Stellar Email Forensic can be of great help. The software offers advanced email search functionality and supports deleted email recovery across more than 25 file formats, including EDB, PST, OST, DBX, NSF, MBOX, OLM, TBB, EML, etc., through a single user interface. Furthermore, this tool preserves the evidence in a legally acceptable format such as PST, MSG, HTML, PDF, EML, etc. In case it turns out that there are large scale after-effects of the cyberattacks, bulk email forensics is required at the organization level.
Are you interested in checking out the features of Stellar Email Forensic software? Download now.
Was this article helpful?