Security researchers at Kaspersky have discovered a new malicious IIS module called Owowa that harvests user credentials when they login to Outlook Web Access (OWA). The stealthy malware lingers on the IIS server to steal credentials when the user authentication request is made via OWA.
Researchers at Kaspersky have identified clusters of Microsoft Exchange Servers targeted by the malware in Asia—mainly in Malaysia, Indonesia, the Philippines, and Mongolia. Most of these servers belong to government organizations.
Besides harvesting user credentials, the malware allows hackers to control the server and run malicious commands remotely.
How Attackers are Using Owowa Malware to Steal Credentials?
Internet Information Services or IIS is a flexible Microsoft web server suite used to serve files and HTML pages. One can extend the IIS functionalities or add features by installing various add-ons called modules—similar to plugins in WordPress or add-ins in Outlook.
Hackers are taking advantage of this and side loading the malicious Owowa module into the IIS server that infects the Exchange Server and exposes the OWA functions.
According to Kaspersky, the attack begins with compromising the unpatched Exchange Server by exploiting the ProxyLogon or ProxyShell vulnerabilities—already patched by Microsoft in March, April, and May 2021.
Attackers then sideload the Owowa module into the IIS web server, which exposes the Outlook Web Access (OWA). As per Kaspersky, the malicious module is first registered in the global assembly cache and loaded by the IIS server running the OWA application.
Once installed, a malicious actor can interact with the loaded Owowa module by executing specifically crafted commands—mentioned below—within the OWA’s Username and Password fields on the authentication page of the compromised Exchange Server.
According to Kaspersky,
- If the OWA username is jFuLIXpzRdateYHoVwMlfc, Owowa will return the encrypted credentials log, encoded in base64.
- If the OWA username is Fb8v91c6tHiKsWzrulCeqO, the malicious module deletes the content of the encrypted credentials log, and returns the OK string (encrypted using RSA).
- If the OWA username is dEUM3jZXaDiob8BrqSy2PQO1, Owowa executes the command that is typed in the OWA password field using PowerShell on the compromised server.
The Owowa responds to these commands via the IIS web server and returns the credentials, timestamp, and users’ IP address to the threat actor in a file encrypted with the RSA algorithm. The user does not notice any error or anything suspicious.
How to Detect and Get Rid of Owowa Malware?
The malicious IIS Module—Owowa—stays persistent even after an Exchange software update, making it an effective tool for attackers. Moreover, it is a much stealthier alternative to phishing emails as it passively steals the user credentials from users accessing the web services.
To detect and identify if your Exchange server is compromised by the Owowa malware, administrators can run the appcmd.exe or IIS configuration tool to retrieve the list of loaded modules on the IIS Server.
The malicious Owowa module uses the ‘ExtenderControlDesigner’ name.
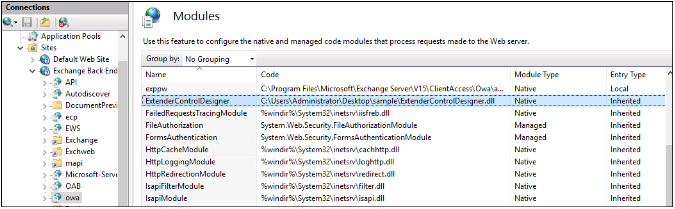
Source: Kaspersky
Remove the IIS module and patch your server immediately by installing the latest Cumulative and Security Updates released by Microsoft for your Exchange Server version.
To learn more, refer to our guide on installing Exchange Server Cumulative and Security updates.
Conclusion
Owowa malware reminds the risks of not installing the Microsoft Exchange Server Security and Cumulative Updates to patch the vulnerabilities. It also highlights the need to check IIS Server modules regularly to check on malicious activities and ensure endpoint security shields are enabled.
In this blog, we have discussed the Owowa malware, its working, and steps to get rid of it. However, it is recommended to set up a new Exchange Server and move mailboxes from your compromised Exchange Server. There can be hidden backdoors or web shells installed by the attacker that can be used to compromise your server or network later.
However, if the server or database is damaged due to a malicious attack, you can use Exchange recovery software, such as Stellar Repair for Exchange, to extract mailboxes from corrupt databases and export them directly to your new Exchange server.
This tool can help you minimize downtime and save you from the huge manual efforts required in recovering and restoring mailboxes. If you need more help, leave a comment or reach us via the Self Help and Support page.
Was this article helpful?