Summary: In this post, we have discussed email investigation techniques- email header analysis, email server investigation, investigation of network devices, sender mailer fingerprints, software embedded identifiers, and bait tactics.
What is Email Forensics?
Email forensics is a branch of digital forensics that focuses on the forensic analysis of email to collect digital evidence for cybersecurity attacks and cyber incidents. It comprises an in-depth forensic investigation of various email aspects such as Message-IDs, transmission routes, attached files and documents, IP addresses of servers and computers, etc.
Email forensic professionals use the following techniques to examine emails and analyze the digital evidence:
Email headers contain essential information, including the name of the sender and receiver, the path (servers and other devices) through which the message has traversed, etc. Some of the critical email header fields are highlighted in Figure 1.
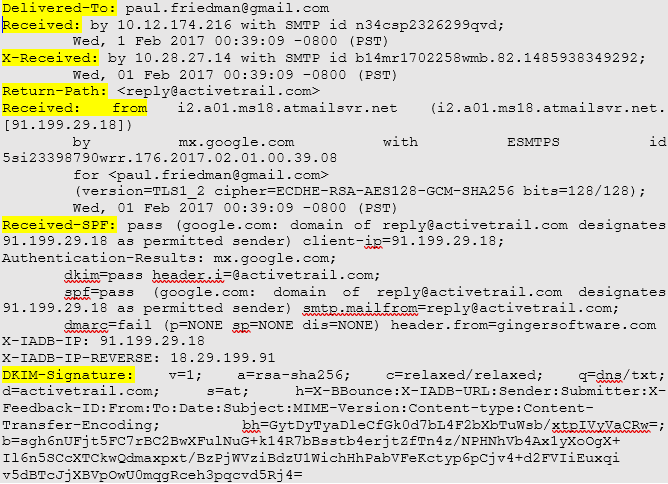 Figure 1: Sample Email Header
Figure 1: Sample Email Header
The vital details in email headers help investigators and forensics experts in the email investigation. For instance, the Delivered-To field contains the recipient’s email address, and the Received-By field contains:
- The last visited SMTP server’s IP address.
- It’s SMTP ID.
- The date and time at which the email is received.
Similarly, the Received: from field provides necessary details like the sender’s IP address and hostname. Again, such information can be instrumental in identifying the culprit and collecting evidence.
2. Email Server Investigation
Email servers are investigated to locate the source of an email. For example, if an email is deleted from a client application, sender’s, or receiver’s, then related ISP or Proxy servers are scanned as they usually save copies of emails after delivery. Servers also maintain logs that can be analyzed to identify the computer’s address from which the email originated.
It is worth noting that Hypertext Transfer Protocol (HTTP) and Simple Mail Transfer Protocol (SMTP) logs are archived frequently by large Internet Service Providers (ISPs). If a log is archived, tracing relevant emails can take a lot of time and effort, requiring decompressing and extraction techniques. Therefore, it is best to examine the logs as soon as possible.
3. Investigation of Network Devices
In some cases, logs of servers are not available. This can happen for many reasons, such as when servers are not configured to maintain logs or when an ISPs refuses to share the log files. In such an event, investigators can refer to the logs maintained by network devices such as switches, firewalls, and routers to trace the source of an email message.
4. Sender Mailer Fingerprints
X-headers are email headers that are added to messages along with standard headers, like Subject and To. These are often added for spam filter information, authentication results, etc., and can be used to identify the software handling the email at the client, such as Outlook or Opera Mail. In addition, the x-originating-IP header can be used to find the original sender, i.e., the IP address of the sender’s computer.
5. Message-IDs
Message-ID is a unique identifier that helps forensic examination of emails across the globe. It comprises a long string of characters that end with the Fully Qualified Domain Name (FQDN). Message IDs are generated by client programs that send emails, such as Mail User Agents (MUA) or Mail Transfer Agents (MTA). There are two parts of a Message-ID. One part is before @, and another part is after @. The first part of the message-ID contains information, such as the message’s timestamp. This information is the data regarding the time when the message was sent. The second part of the Message-ID contains information related to FQDN.
6. Embedded Software Identifiers
Sometimes, the email software used by a sender can include additional information about the message and attached files in the email. For example, it can be found in Multipurpose Internet Mail Extensions (MIME) content as a Transport Neutral Encapsulation Format (TNEF) or custom header. An in-depth analysis of these sections can reveal vital details related to the sender, like the MAC address, Windows login username of the sender, PST file name, and much more.
7. Bait Tactics
The bait tactic is an email investigation technique used when the location of a suspect or cybercriminal is unknown. In this, the investigators send the suspect an email containing an http: “<img src>” tag. The image source is on a computer that the investigators monitor. When the suspect opens the email, the computer’s IP address is registered in a log entry on the HTTP server that hosts the image. The investigators can use the IP address to track the suspect. Sometimes, suspects take preventive measures like using a proxy server to protect their identity. In that case, the IP address of the proxy server is recorded. However, the log on the proxy server can be analyzed to track the suspect.
If the log isn’t available either, then the investigator can send an email that contains either of the following:
- HTML page with an Active X Object.
- Embedded Java Applet that is configured to run on the recipient’s computer.
Both of these can record the IP address of the suspect’s computer and send the same to the email address of the investigators.
8. Bulk Email Forensics
Large mailbox collections are often examined, analyzed, and used as evidence in legal cases. Therefore, legal professionals have to work with large mailboxes in many cases. Most email service applications, like Outlook and Gmail, offer a dashboard embedded with several valuable functions. However, you may not get the desired results by only using keywords in the interface.
Date and time are two attributes of emails considered necessary when they are produced as evidence related to a case. However, emails can be forged like physical documents, and hackers may tamper with these attributes. In addition, since an email doesn’t directly reach from the receiver to the sender, recording its actual route with accurate timings is a tricky aspect.
9. Importance of using Hashing Algorithm
MD5 and SHA1 are the two most crucial hashing algorithms used by digital forensics professionals. It’s a standard practice to use MD5 and SHA1 hashing algorithms in email forensics investigations. These algorithms allow forensic investigators to preserve digital evidence from the moment they acquire it until it is produced in a court of law. Another reason why hash values are important is that electronic documents are shared with legal professionals and other parties during the investigation. Therefore, ensuring that everyone has identical copies of the files is crucial.
Email forensics investigation can be a complicated task when there are many suspects involved and required analysis of a large number of email mailboxes. That’s why professionals use enterprise-grade eDiscovery and advanced email investigation tools, such as Stellar Email Forensic, for fast and accurate analysis. Stellar Email Forensic comes equipped with features like multiple email views, advanced keyword search filters, deleted emails recovery, bulk email forensics, preservation of digital evidence with MD5 and SHA1 hashing algorithms, etc. These programs also generate evidence reports and offer case management during criminal investigations through tagging, bookmarking, and log management to manage multiple and large mailboxes easily.
Download a free trial of Stellar Email Forensic software to start your email investigation now. The software is available for a free 60-day trial, offering all features unlocked in the demo version.
Was this article helpful?