Circular logging is usually used to truncate the database logs in the databases. By default, in Exchange Server, when an application backup is executed and successful, the system will automatically purge the unneeded transaction logs from the database, thus freeing up some space. If your backup is not purging the logs, this means that the transaction logs will never be purged and end up filling up your storage to the bin, ending up with no incoming or outgoing emails and users will be unable to save anything in their databases or public folders. This could also lead up to data corruption. A big number of transaction logs are generated during the day. Transaction logs are important for the health of the database as these hold temporary data and are used as a buffer between the Exchange Server database and the users to keep the database healthy and perform well.
An easy way to solve the storage issue would be to take a backup. If there is no space, the only alternative is to enable circular logging to truncate the logs and re-enable them again. Circular logging is disabled by default.
Here, we’ll be discussing the methods to disable the circular logging in Exchange Server:
Methods to Disable Circular Logging
You can disable circular logging by using the Exchange Admin Center (EAC) or Exchange Management Shell (EMS).
Note: Microsoft and many engineers strongly recommend not to disable circular logging as it may cause issues.
1. Use Exchange Admin Center (EAC)
To disable circular logging using the EAC, follow these steps:
- Once you logged into the Exchange Admin Center (EAC)with your administrative user, click on Servers. On the main page, click on Databases, select the desired database, and click on the Edit button.
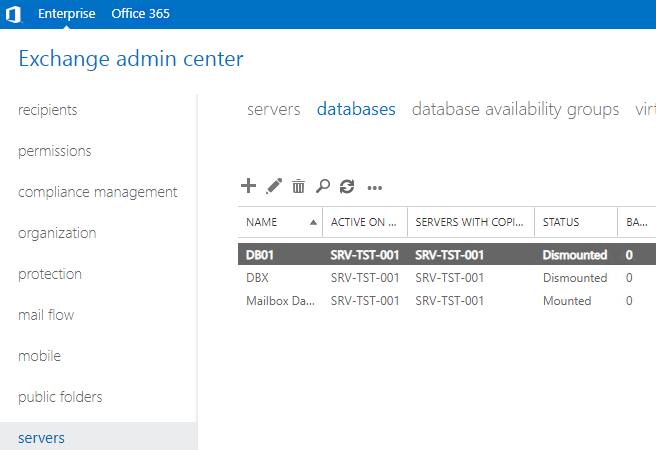
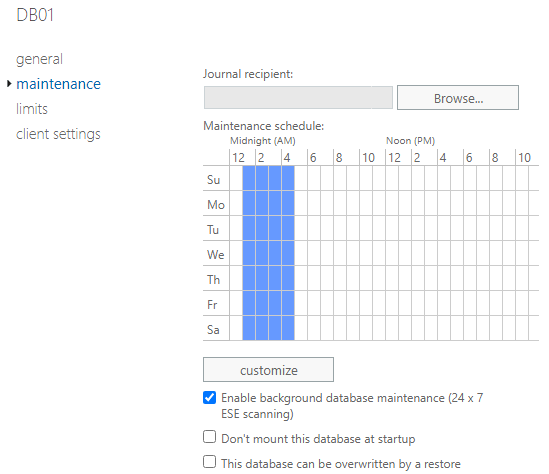
- If you don’t see the option to enable circular logging, just scroll down and tick Enable circular logging.
- Click Save.
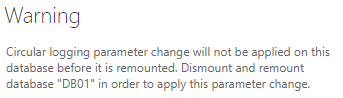
- When you click on the Save button, you will be get a prompt saying, for the change to be in effect you will need to dismount the database and mount it again. Once you click on the OK button, you need to dismount the database and remount it manually.
- This can be done by selecting the database in question. Click on the more options and click on Dismount.
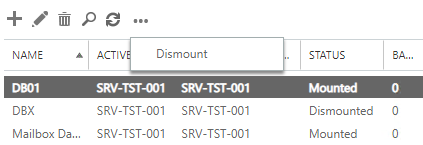
- After some time, you should see that the transaction logs are purging automatically. After you have the necessary storage, you will need to re-do the same operation to mount it. Click on the database in question, click on more options, and then click on Mount.
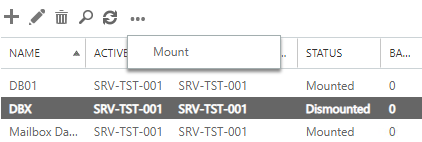
The same operation is needed to disable circular logging, i.e., open the database, disable circular logging, and then dismount and mount Exchange database.
2. Use PowerShell
Alternatively, you can use the PowerShell commands to enable circular logging. You can use the parameter $False to disable and $True to enable.
Open the Exchange Management Shell (EMS) and use the below commands:
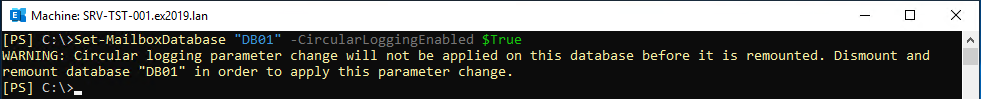
Set-MailboxDatabase "<database name>" -CircularLoggingEnabled $True
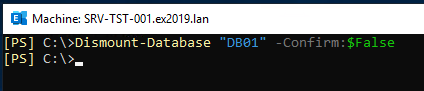
Dismount-Database "<database name>" -Confirm:$False
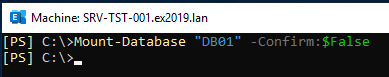
Mount-Database "<database name>" -Confirm:$False
To Conclude
Make sure that you do a backup of the logs and Exchange database before performing any activity on Exchange log files. There are chances of Exchange database corruption and Database may not dismount or remount after disabling circular logging. You can also face such type of errors:
- “Microsoft Information Store”. Advance Open File Option used: Microsoft Volume Shadow Copy Service (VSS).
- Incremental and differential backups are not possible because Microsoft Exchange is configured for circular logging.
Stellar Repair for Exchange will be of assistance in such sticky situations. With Stellar Repair for Exchange, you don’t need to worry about how to execute Exchange server recovery on any version without any complex recovery processes or number of applications. This application is all you need for all the necessary work on your Exchange Server. With Stellar Repair for Exchange, you can open multiple databases hosting public folders, mailboxes, disabled or shared mailboxes. The application can open corrupt database from any Exchange Server version without having Exchange installed.
So, what’s so special about this application apart from opening multiple EDB files? Well, once you open an EDB file and after a quick scan, you will see the whole structure of the database, along with the ability to browse through it. It has a very familiar and easy interface with the structure on the left, middle pane for the email list with in-built and in-line search, and the full HTML preview pane on the right. You can also view the calendars, contact, tasks, or journals. You can export the recovered database to PST and other file formats, such as EML, HTML, MSG, and PDF.
With Stellar Repair for Exchange, you can easily recover an orphaned or damaged database. You can export the recovered database directly to a live Exchange Server database or Office 365 tenant. Other great features include parallel recovery, VIP list (a set of important mailboxes or public folders), memory optimization, and continuation of process if the application is interrupted.
Was this article helpful?