BlackCat, also known as ALPHV or Noberus, was first observed in November 2021. It is one of the first ransomware developed with the Rust programming language. Modern programming helps the ransomware evade detection from specific security solutions that may fail to parse or analyze the RUST binaries (payloads).
Known for targeting and encrypting Windows, Linux, and VMWare instances, the BlackCat ransomware group is now exploiting the unpatched and vulnerable Microsoft Exchange Servers to gain access to the targeted organizations’ networks.
In this blog, you will learn the tactics and techniques used by the BlackCat ransomware to target and exploit vulnerable Exchange Servers and how to safeguard your servers or networks from the ransomware.
How BlackCat Ransomware Gang is Exploiting the Exchange Servers?
BlackCat ransomware gang runs Ransomware-as-a-Service (RaaS) scheme, providing other attackers access to their malicious code and infrastructure to exploit the targeted networks or servers. In return, the gang negotiates the ransom with the victims and shares a specific ransom amount with the attackers. Thus, anyone accessing a compromised Exchange Server environment can use the BlackCat ransomware samples to infect the server and encrypt the data for a ransom.
The BlackCat ransomware group claims to be the rebranded successor to the notorious BlackMatter and REvil ransomware groups. It uses several similar tactics and techniques to attack and infiltrate Exchange Servers.
- The payload is written in cross-platform Rust language, allowing them to create versions of malware to target and infect both Windows and Linux environments.
- They use a modified Fendr utility called ExMatter — a custom exfiltration tool (originally used by the BlackMatter group) to extract the data from the targeted or compromised Exchange Server.
- It also utilizes the PsExec tool — a portable tool to run processes or codes remotely using any user’s credentials — for lateral movements in the compromised network.
- Password extractor tools such as Mimikatz and Nirsoft to extract passwords.
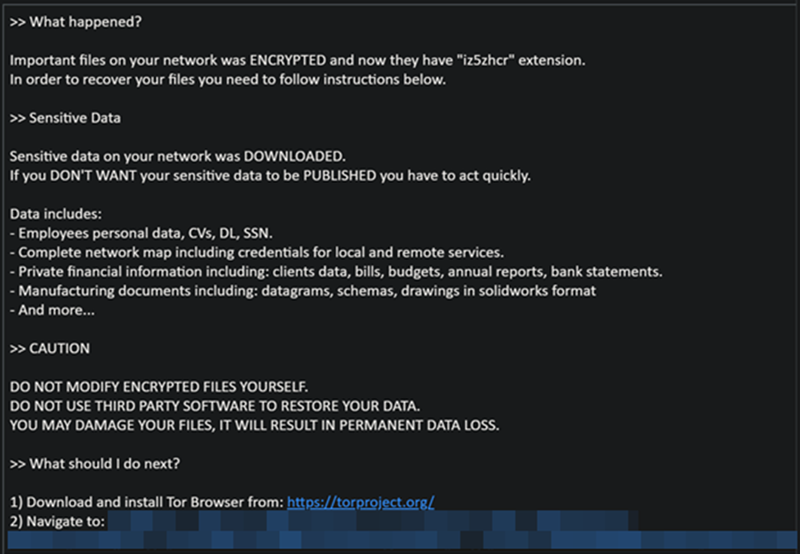 Image Source – microsoft.com
Image Source – microsoft.comThere is at least one known BlackCat ransomware attack incident on a vulnerable Exchange Server observed by Microsoft’s security researchers. The attackers moved slowly into the victims’ network, stole the credentials, and exfiltrated the information to use it for extortion or ransom.
Later, the threat actor deployed the BlackCat ransomware payload using the PsExec tool. Although the threat actors used the entry vectors, such as remote desktop applications and stolen credentials, they also exploited the Exchange Server vulnerabilities to gain access to the target network.
How to Protect your Exchange Server Environment from BlackCat?
To protect and safeguard your Exchange Server and network infrastructure from such ransomware, follow the best security practices and policies with advanced Exchange-aware protection capabilities to detect and block such attacks. Most importantly, upgrade your Exchange Server to the latest Cumulative Updates and install the latest Security Updates to patch the vulnerabilities. If you are running an older Exchange version, such as 2010, it is recommended that you immediately upgrade to a latest version, preferably Exchange Server 2016 or 2019.
In addition, follow the below steps to check the server health, find vulnerabilities, and patch them.
Step 1: Use Exchange Server Health Checker PowerShell Script
You can download the Microsoft Exchange Server Health Checker Script or HealthChecker.ps1 script from the official GitHub page and follow the steps below to execute it on your Exchange Server 2013, 2016, or 2019 to find health issues and vulnerabilities and fix or patch them to safeguard the server.
- Open the Exchange Management Shell (EMS) and execute the following command to prevent error while running the HealthChecker.ps1 script.
Set-ExecutionPolicy -Scope Process -ExecutionPolicy Bypass
- After downloading the HealtHChecker.ps1 script, navigate to the folder location where the script is downloaded using the ‘cd ‘command in EMS. For instance,
cd C:\Users\UserName\Downloads\
- Then run the following command to execute the script on the server.
.\HealthChecker.ps1
- You may also execute the script with –BuildHtmlServersReport parameter to generate a detailed HTML report.
.\HealthChecker.ps1 –BuildHtmlServersReport
- The HTML file will be saved in the same folder where the script is located. You can open the HTML file in any web browser, such as Google Chrome or Microsoft Edge.
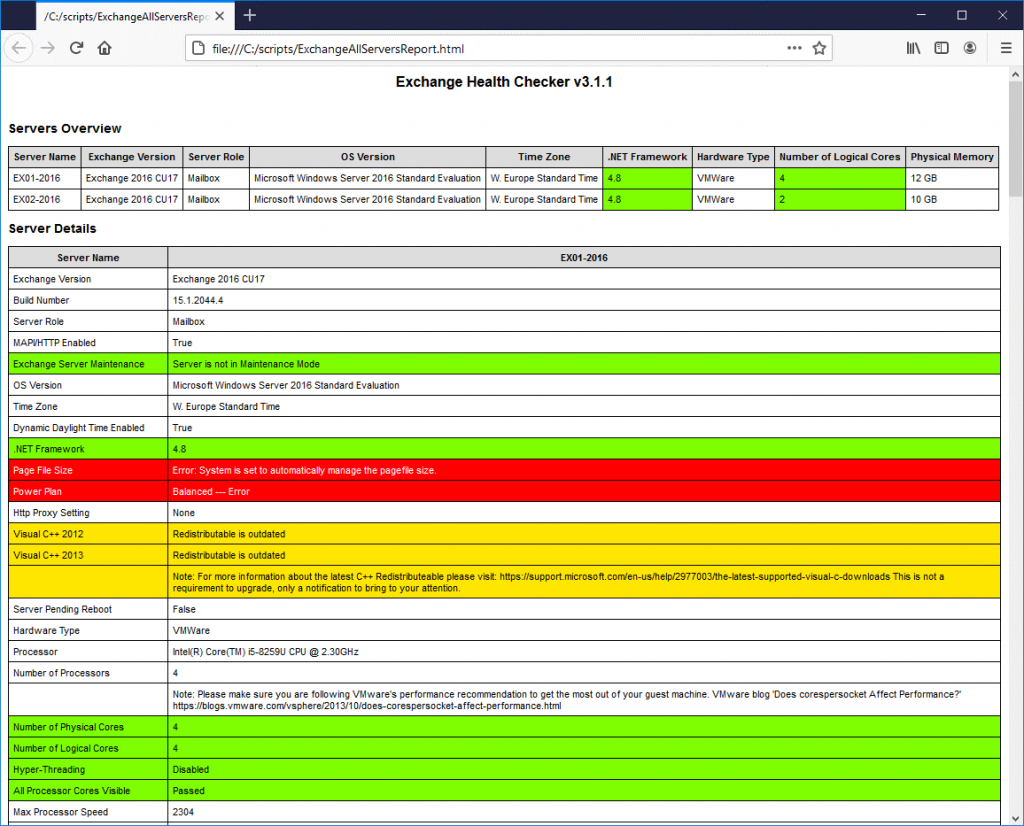
- Check the entries highlighted with Red and fix them as soon as possible. Also, check the vulnerabilities section for pending Security Updates you need to apply to patch the Exchange Server.
Step 2: Install Exchange Server Updates
If the report shows vulnerabilities, use the links in the HTML report to download and install the updates. You can also refer to our detailed guide to download and install the latest Cumulative Updates and Security Updates on your Exchange Server.
Conclusion
Ransomware gangs often target unpatched and vulnerable Microsoft Exchange Servers to compromise the network and encrypt the devices or data to extort ransom. For example, BlackCat is a ransomware group that deploys ransomware on compromised networks. According to Microsoft 365 Defender Threat Intelligence Team, the threat actors leverage the Exchange Server vulnerabilities to gain access to the target network.
Thus, the best defense against BlackCat and similar malicious attacks is to install the latest Cumulative and Security updates released by Microsoft as soon as possible. However, if your server is compromised or crashed due to BlackCat or any other ransomware attack, set up a new Exchange Server and restore the mailbox databases from the backup.
If the backup isn’t available, recover the mailboxes from the databases on the compromised server with the help of Exchange recovery software, such as Stellar Repair for Exchange, and restore them to the newly setup server.
To stay updated on newer Exchange Server threats, vulnerabilities, and updates, follow our consistently updated blog on Microsoft Exchange RCE Vulnerability Flaws and Their Fixes.
Was this article helpful?