Summary: Investigation of unsolicited commercial email cases can be pretty challenging due to the sheer number of emails involved and the complexity of each email infrastructure. For instance, you have to record the correct dates and times of hundreds or thousands of emails along with other details, like IP addresses of senders and receivers, mail servers, attachments used, etc. However, the biggest obstacle is timing – the legal system follows tight deadlines. Therefore, you usually don’t get enough time to look through thousands of emails from one or more mailboxes for data collection and case report preparation. Hence, for legal cases involving emails, a different approach is needed. Forensic analysis of such emails can be done using an advanced eDiscovery tool, such as Stellar Email Forensic.
Large email collections are often examined and used as evidence in legal cases. For instance, in cases of unsolicited commercial emails (UCE), a company may accuse another company of violating anti-spam laws on account of sending spam emails. So, legal professionals have to work with bulk emails in such cases. In this article, we will discuss the techniques followed for the manual examination of bulk emails and, as a result, the challenges the investigators face by taking a case of unsolicited commercial emails as an example.
Overview
Unsolicited commercial emails are promotional emails, also known as spam emails, sent to recipients on a large scale without their consent. Marketing companies or advertising agencies usually send these emails to email users with the help of extensive mailing lists.
In many countries, there are strict laws against unsolicited commercial emails, and hefty fines are levied on the guilty in violation of the same to limit spam emails and curb phishing attacks. Unfortunately, some entities exploit these laws for personal gain – they are often tempted to create massive collections of fraudulent emails so that they can file cases against the marketers and claim large cash settlements. It is not uncommon for plaintiffs to assert damages worth millions of dollars when they claim to receive and collect thousands of emails over time from a particular company.
In this article, we take the example of a legal case in which a company (the plaintiff) has claimed to have allegedly received thousands of spam emails from an advertisement company (the defendant). We will mainly focus on the defense’s perspective and discuss the challenges you may face as a legal professional while examining bulk emails.
Remember, the goal is to prove that fewer emails violated the laws than the number claimed by the plaintiff so that the penalty is minimized and the punishment attenuated.
Techniques and Challenges in Bulk Email Forensics
1. Search Operators
Most email service applications, like Outlook and Gmail, offer an intuitive dashboard embedded with several useful functions. One of these is the search box feature, which you can use to examine the mailbox. However, you may not get the most accurate results by feeding raw keywords into the tool. Instead, a better approach is to use search queries that can be fed to the search box. Microsoft Outlook, for instance, works with Advanced Query Search (AQS) language to help you quickly find the emails and attachments that you are seeking. Some examples of Outlook Instant search queries are as follows:
| AQS Keyword | Details | Query Example |
|---|
| From | Searches the from field | From:John |
| Subject | Searches the subject | Subject:file |
| HasAttachment:yes | Searches and displays only those emails that have attachments. You can filter the messages further by adding search keywords. For example, report hasattachment:yes will display only those emails that have attachments and the word “report” in the messages | hasattachment:yes |
Just like Outlook, Gmail also offers similar search functions.
Search functions can help you filter thousands of emails quickly and make investigation easy. However, manually entering a wide range of keywords and search queries consumes a lot of time. More importantly, there is a margin of error that you cannot overlook. For instance, you may scan a mailbox and count 1,224 emails that are relevant, but you are off by just two emails. This difference isn’t huge for an average user. However, when it comes to legal matters, even a minor discrepancy like this can completely change the outcome of a case. If anything, inaccuracy in your records can lower your credibility and give the plaintiff an upper hand. So, it’s strictly advised that you use a professional eDiscovery or forensics email examination software that can identify every single email that exists in a database.
2. Date and Time Documentation
Date and time are two attributes of emails considered important when they are produced as evidence related to a case. However, emails can be forged just like physical documents, and the culprit may tamper with these attributes. Since an email doesn’t directly reach from the receiver to the sender, recording its actual route with accurate timings can be tricky. This is because emails usually move from one hop to another and each server stamps its own date and time on the email header.
If someone has tampered with the emails, then you have to demonstrate the same with comprehensive records and reports. One way to do this is to analyze the Receiver field in the email headers of the messages, as it can show the arrival times of the email at all the servers. Consider this snippet from an email header:
 Figure 1: Sample Email Header Snippet
Figure 1: Sample Email Header SnippetFinding Received fields in the email headers of a few messages isn’t tricky. However, if there are thousands of emails to examine, performing the task can pose serious challenges. Apart from the Received field, there is another important field called Message-ID. Message IDs also help investigators in extracting useful information. Apart from these, it can be of great help if you have advanced software for email search that can highlight the important details of an email in a single click. Plus, there can be discrepancies if the plaintiff has deleted some emails.
Suppose you are able to gain access to the plaintiff’s email account on legal grounds. In that case, you can recover deleted emails from the Deleted Items folder (most email applications and services offer this feature). Otherwise, you have to take a more advanced approach. For instance, in Microsoft’s Outlook, you can go to the user’s account, select Recover Deleted Items From Server from the dashboard (See Figure 2), and select the items you want to recover. However, if emails are permanently deleted, you can only recover them with an email forensic software that can recover deleted emails or recover deleted mailbox data (in case the entire mailbox has been deleted).
 Figure 2: Recover Deleted Items from Server Option in Outlook
Figure 2: Recover Deleted Items from Server Option in Outlook3. Detection of Duplicate Emails
Duplication in emails can be identified if two files are compared byte-by-byte and found identical. For this, popular hash values, like SHA-1 and MD5, which are unique identifiers of the files, are compared. However, there can be emails that are partial duplicates, i.e., only certain details are identical. So, maybe two emails have identical byte sequences except for the Received headers, or there may be differences in the byte sequences of the attachments.
The problem with identifying duplicate information, especially when only partial content is replicated, is the manual nature of the task. Manually scanning large volumes of emails is a cumbersome task. Therefore, enterprise-grade email examiner tools can be of great help here as they can identify and share distinct factors, like hash values, unique message IDs, hex values, etc.
4. Parsing Emails
Email headers hold essential information, such as senders’ and receivers’ IP addresses, dates and times, message transfer agents, etc., that can be used in forensic investigation and litigation. However, email headers in their raw form lack structure and organization. Check out a snippet of an email header in the image below:
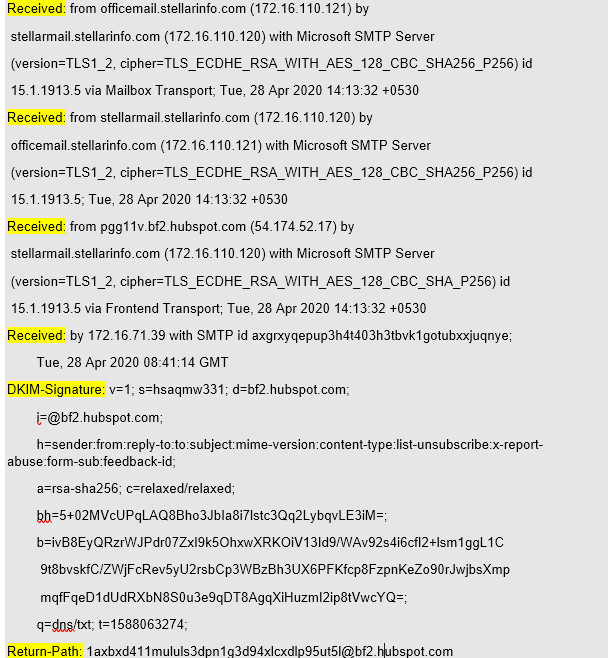 Figure 3: Snippet of a Sample Email Header
Figure 3: Snippet of a Sample Email HeaderTo extract important data quickly and efficiently, you need to group different sections of an email. This can be most viably done with an advanced case management software that can group extracts for comparative analysis. Once you have all the emails organized into different views, like attachments, Internet header, etc., you can clearly view the involved message transfer agents, messaging protocols, transmission routes, etc.
How does using advanced software for email search help?
Competent legal professionals don’t shy away from challenges. Well-versed in respective laws and equipped with a wide range of litigation techniques, they can turn some of the most challenging cases in the interest of their clients. However, when it comes to investigating and collecting digital evidence in an unsolicited commercial email case, they may find themselves struggling in the absence of adequate tools and resources. Stellar Email Forensic is a powerful email forensics tool that can fill this gap.
Stellar Email Forensic software can make your legal firm future-ready and drive business because it:
- Can analyze and examine more than 25 email file formats. Once you have Stellar Email Forensic software, you don’t need any other tool for a particular email service because all the mailboxes, such as EDB, PST, OST, DBX, NSF, MBOX, OLM, etc., are seamlessly extracted, recovered, and analyzed through this software.
- Comes packed with powerful features, like advanced searches, such as Boolean Search, Regular Expression Search, deleted emails recovery, case management during criminal investigation, report generation, multiple email views, like, Hex, hash values, HTML, RTF, Internet Header, etc., and many more.
- Apart from this, you can export data into PST, Office 365, Live Exchange, MSG, and EML file formats.
- It saves your precious time in examining, investigating, and collecting emails, which can be used to work on other cases. You also get to focus on building your case rather than spending hours collecting evidence from massive mailboxes. Since time is of the essence when it comes to legal matters, you want the fastest solution possible.
- It helps you protect your credibility. The software is not only fast, but it’s also incredibly accurate. So, all your reports and evidence files are court-admissible and devoid of discrepancies.
You can download the complete software here.
Take Away Points
Summarizing the information in this article, we can establish that legal cases involving emails in bulk need a different approach than cases involving fewer emails. We can draw the following conclusions:
- You should analyze digital evidence such as bulk emails with automated tools and techniques, although not at the cost of accuracy.
- You must go to great lengths to ensure that there are no mistakes in examination and evidence collection. Even small mistakes can snowball into big challenges when the volume is high.
- Not only should you identify and collect relevant emails, but you should also organize them with tags and bookmarks for speedy investigation.
The above-discussed methods and techniques can greatly help legal professionals when dealing with cases such as unsolicited commercial emails or others involving forensic analysis of emails. However, some techniques have limitations when it comes to examining thousands of emails. Therefore, a specialized eDiscovery and email forensics software can make working with bulk emails simple and easy.
Was this article helpful?