The Kernel-mode hardware-enforced stack protection is a security mechanism within the Windows OS. It is designed to safeguard your PC from various attacks that might exploit some memory stack vulnerabilities. This feature is turned off by default on your system and you need to enable it manually.
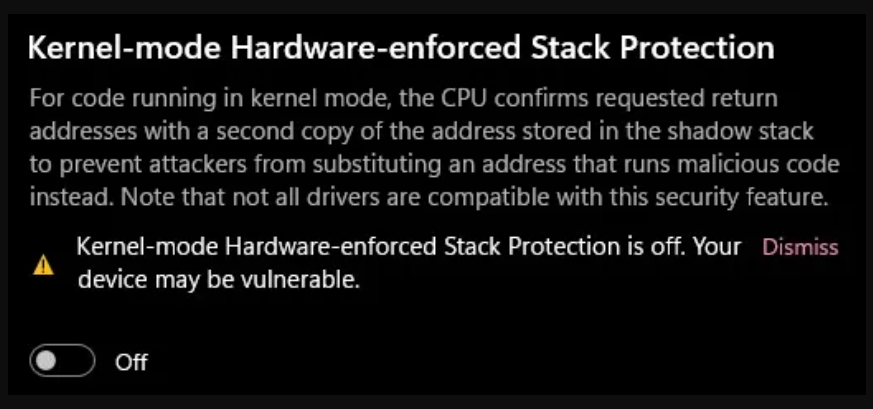
However, after updating Windows Defender on their PC, some users reported facing a warning message that reads: “Kernel-mode Hardware-enforced stack Protection is off.” Even if the users try to enable this feature manually, the feature may still appear disabled; this could be due to issues with drivers or anti-cheat software used by computer games.
Are you facing a similar problem on your Windows PC? This blog looks at this issue in detail and offers workable solutions to effectively resolve it. Let’s get started.
Understanding Kernel-Mode Hardware-Enforced Stack Protection
A kernel acts as a bridge between software applications and the hardware to ensure efficient communication between the two. To prevent this core component of the OS from getting hijacked by an attacker, Windows introduced the kernel-mode hardware-stack protection feature.
- The feature uses “shadow stacks” to keep track of the flow of programs running on your system. If an attacker attempts to modify this flow to execute a harmful code, the system quickly detects it and thwarts the attack.
- It safeguards against sophisticated exploits, such as Return-oriented Programming (ROP) and Jump-oriented Programming (JOP).
- It leverages support from compatible CPUs to monitor and validate safe operation sequences for software processes on your computer.
Now that you understand what kernel-mode hardware-enforced stack protection does, you might be wondering whether you should turn it on? The short answer is yes, and for all the valid reasons – It adds an additional layer of security that protects your system from common exploits, prevents an attacker from unauthorized code execution, and maintains the overall integrity of your system by securing the kernel.
Fixing the Kernel-Mode Hardware-Enforced Stack Protection is Off Issue
Before attempting to fix the issue, you are recommended to update to the latest BIOS that supports Control-flow Enforcement Technology (CET), a prerequisite for enabling kernel-mode hardware-enforced stack protection.
To do this, go to your motherboard manufacturer’s website, download the latest BIOS version and copy it onto a USB flash drive. Now follow the steps below:
Step 1: Plug and USB flash drive into your PC and go to Settings > Update & Security.
Step 2: Click Recovery from the left sidebar.
Step 3: Under Advanced startup, click Restart now and wait till Windows boots into Advanced Startup Options.
Step 4: Now, click Troubleshoot and select Advanced options.
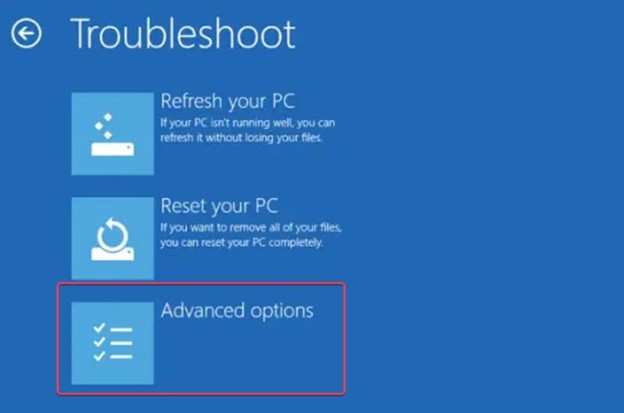
Step 5: Click UEFI Firmware Settings and hit Restart. Your Computer will now boot to BIOS.
Step 6: Once you enter BIOS, find the BIOS update option and select it.
Step 7: Lastly, select the BIOS update file from your USB drive and wait for the process to complete.
Now, you are ready to proceed with the troubleshooting steps below.
Method 1: Enable VBS and HVCI
Before enabling kernel-mode hardware-enforced stack protection, ensure that Virtualization-based Security (VBS) and Hypervisor-enforced Code Integrity are enabled. Here’s the rundown:
Step 1: Open the Windows Security app.
Step 2: Go to Device Security > Core isolation details > Memory integrity.
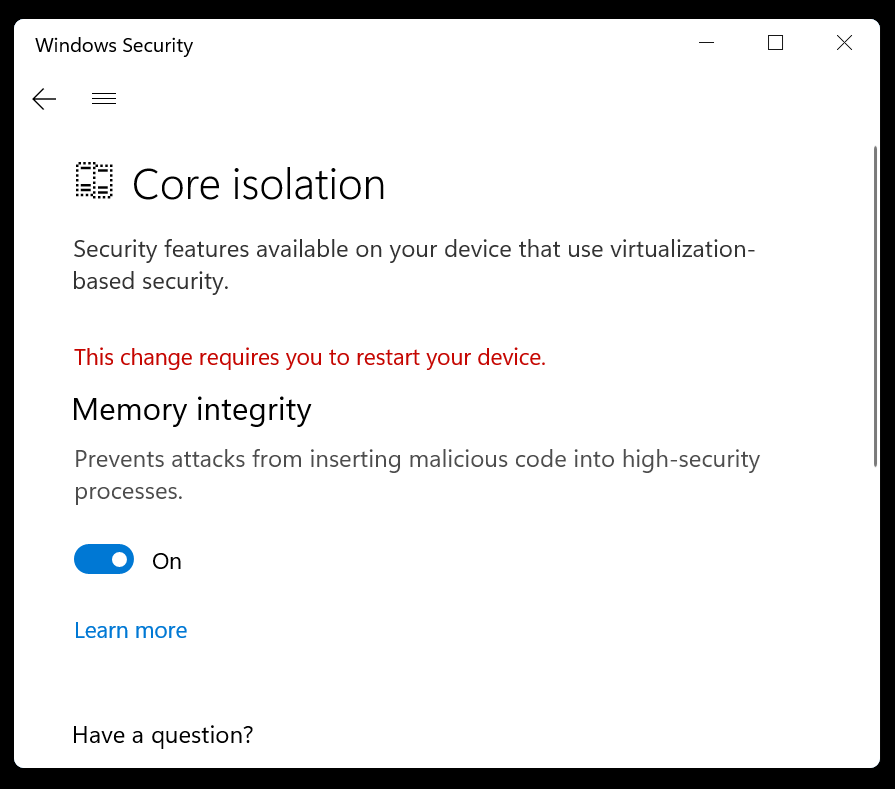
Step 3: Toggle On the feature and restart your computer.
Method 2: Enable CPU Virtualization in BIOS
At times, turning on kernel-mode hardware-enforced stack protection requires CPU virtualization capabilities. Follow the steps below to enable CPU virtualization:
Step 1: Restart your PC and press F2 or Del to enter BIOS.
Step 2: Navigate to virtualization settings; they may be under Advanced CPU configuration, Chipset, or Security.
Step 3: Locate and turn on the virtualization option named VT-x, AMD-V, or SVM.
Method 3: Modify Windows Registry
Windows Registry is a hierarchical database that stores low-level settings for programs and hardware installed on the Windows operating system. Changing certain settings within the Windows registry may help you enable kernel-mode hardware-enforced stack protection on your PC.
Note: Making changes to the Windows Registry can affect the files on your computer and may even cause data loss. We recommend backing up before you attempt this method.
Here’s how to modify Windows Registry on your PC:
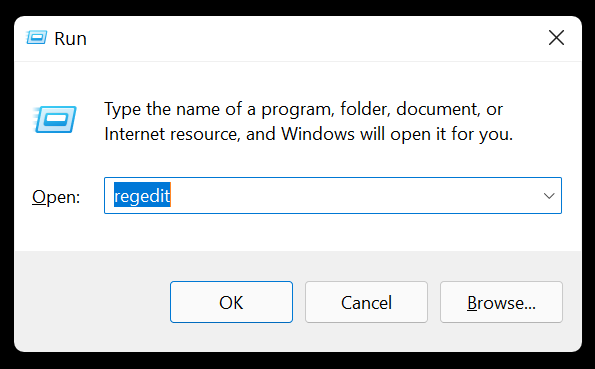
Step 1: Press Win + R to open the Run dialog box.
Step 2: Type in regedit and click OK.
Step 3: Now navigate to the following path: HKEY_LOCAL_MACHINESYSTEMCurrentControlSet\Control\Session Manager\Memory Management
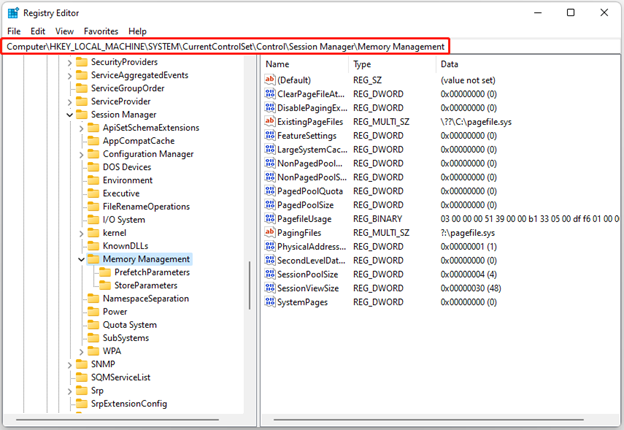
Step 4: Locate FeatureSettingsOverride and double-click it.
Step 5: Select DWORD (32-bit) Value and name it FeatureSettingsOverride.
Step 6: Double-click on it, set the value to 9 and click OK.
Step 7: Close the Registry Editor and restart your PC.
Method 4: Uninstall Confliction Applications, Drivers or Extensions
Using incompatible software, such as an anti-cheat system used by many games, may cause conflict and prevent the kernel-mode hardware-enforced stack protection feature from turning on. However, it’s difficult to pinpoint the exact application, driver, or extension that might be the culprit behind this.
To resolve this, head over to the Control Panel or Settings to review your installed apps. Look for any recent software installation that might be causing the issue. Uninstall these apps one at a time, and after each uninstallation, try turning on the kernel-mode hardware-enabled stack protection again to see if it works.
Method 5: Enable DEP
Data Execution Prevention is a different security feature that works well alongside kernel-mode hardware-enforced stack protection by stopping the code from running in non-executable memory areas. Here’s how to enable DEP on your computer:
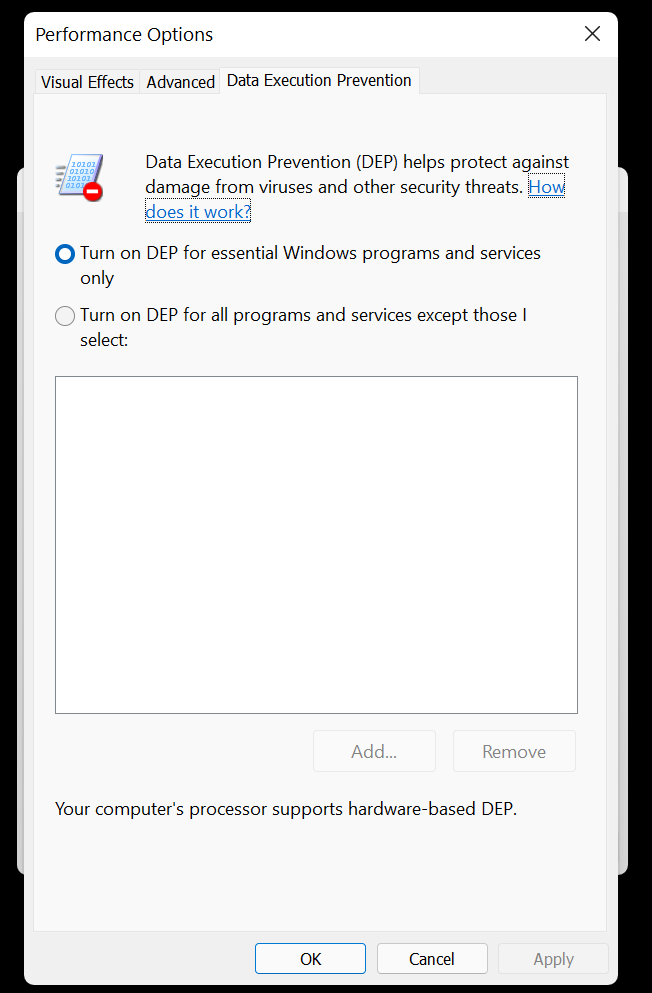
Step 1: Right-click on This PC, select Properties and then go to Advanced system settings.
Step 2: Under Performance, click Settings, and go to the Data Execution Prevention tab.
Step 3: Based on your requirement, select either Turn on DEP for essential Windows program and services only or Turn on DEP for all programs.
How to Recover Lost Data After Facing the Kernel-Mode Hardware-Enforced Stack Protection is Off Issue?
Kernel-mode hardware-enforced stack protection is a security feature that prevents attacks that modify return address in kernel-mode recovery. If this feature gets disabled, it can make your computer’s data and applications vulnerable to data loss, as an attacker can use the opportunity to launch malicious code on your system.
If you have recently faced the “kernel-mode hardware-enforced protection is off” issue on your PC, and notice any data loss on your PC, it could due to the execution of a malicious code that might have deleted the files from your system. In such cases, we recommend using a professional data recovery software to reclaim your lost files.
Bottom Line
Kernel-mode Hardware-enforced stack protection is off issue mainly occurs after updating the Windows Defender or due to conflicting software, like anti-cheat systems used by certain games. You can re-enable this feature by following the troubleshooting methods mentioned above. Additionally, remember to back up your system beforehand to prevent any data loss.
What is shadow stack?
Shadow stack is a parallel hardware stack that prevents control-flow hijacking by maintaining a separate and protected copy of the return addresses for function calls. It is a security feature in Windows designed to protect the integrity of a program’s control flow.
Was this article helpful?