Microsoft has identified a zero-day vulnerability in Exchange Server, which attackers are already exploiting. At the time of releasing February’s Patch Tuesday update, Microsoft has internally tracked the CVE-2024-21410 vulnerability that impacts the elevation privilege on the vulnerable Exchange Servers. This zero-day vulnerability primarily impacts Exchange Server 2016 and 2019. The vulnerability allows the threat actors to force network devices, including domain controllers and servers, to authenticate against a New Technology LAN Manager (NTLM) relay server, controlled by them, to imitate the targeted devices and elevate the privileges. NTLM protocol is normally used for authentication, integrity, and confidentiality of the Active Directory/Exchange Server mailboxes.
By exploiting the vulnerability, the attackers target NTLM clients, such as Outlook, to gain access to the victim’s credentials. These leaked credentials are then used to gain privileges as the victim and to perform operations on the Exchange Server on the victim’s behalf. This means that a successful attacker can impersonate the user using the Net-NTLMv2 hash. The attackers can get access through a user who has admin access to the Exchange Server and modify the configuration or leak the data. If data is compromised, the impacted organizations can also face legal actions for not protecting the services and data of the clients.
How to Mitigate or Protect against this New Vulnerability?
You need to enable the NTLM credentials Relay Protections, also called Extended Protection for Authentication (EPA), to address the CVE-2024-21410 vulnerability. The Extended Protection (EP) is a protocol that is used to strengthen the Windows Server authentication functionality, thus mitigating such attacks.
For Exchange Server 2019, you can install the 2024 H1 Cumulative Update or CU 14, released by Microsoft on Patch Tuesday (on February 13, 2024). In this update, Microsoft has announced that the Exchange Extended Protection Management (EP) is automatically enabled in the CU 14 and onwards.
However, in previous Cumulative Updates of Exchange Server 2019, the New Technology LAN Manager (NTLM) credentials Relay Protections were not enabled by default. So, you need to install the latest Cumulative Update (CU) 14 as soon as possible to mitigate the vulnerability.
For Exchange Server 2016, first install the latest Cumulative Update (CU) 23 and then download the Exchange Extended Protection Management PowerShell script. This will automatically set up and configure the Extended Protection (EP) option on Exchange Server.
Check the Exchange Server Health
To confirm that the Exchange Server is protected, after installing the latest Cumulative Update (CU), you must run the Exchange Server Health Checker script. Downloaded the Health Checker script and run the script by using the below cmdlet:
HealthChecker.ps1
To run the script against a remote server, use this cmdlet:
HealthChecker.ps1 -Server <server name>
To run the script against multiple servers, you can execute the cmdlet as given below:
HealthChecker.ps1 -Server <server name, server name, server name>
Note: In above cmdlet, separate the servers name with commas.
The HealthChecker.ps1 script will give a lot of information about the status and upkeep of the Exchange Server, as well as the status of the Extended Protection (EP) feature.
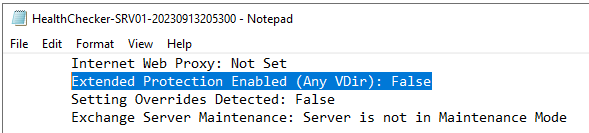
Extended Protection Enabled (Any VDir): False
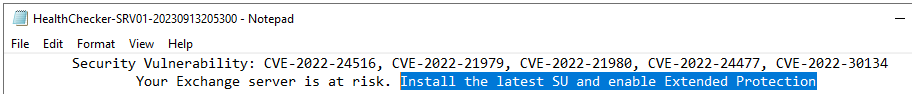
Security Vulnerability: CVE-2022-24516, CVE-2022-21979, CVE-2022-21980, CVE-2022-24477, CVE-2022-30134
Your Exchange server is at risk. Install the latest SU and enable Extended Protection
In addition, ensure that antivirus and firewalls are installed, and good backup system and failover system are in place.
How to Recover Data if the Exchange Server gets Compromised?
In case your Exchange Server gets compromised or attacked by ransomware/malware, you can isolate your server from the network and create a new server. Then, you can restore the databases on the new server. But this involves a lot of time and administrative efforts. However, if the database gets damaged or corrupted, you can rely on backups but this means losing some of the data (from when the backup was taken to when the server was compromised).
Another option to recover the data in the least possible time is by using an Exchange Recovery tool, like Stellar Repair for Exchange. This application helps to extract mailboxes from the compromised/failed Exchange Server or corrupted databases and export them to a new live Exchange Server.
To Conclude
Microsoft has informed us about a new zero-day vulnerability – CVE-2024-21410 in Exchange Servers and also released the Cumulative Update to fix this vulnerability. So, it is important to install the latest update to mitigate the vulnerability and protect against any malicious attacks. When installing the Cumulative Updates, it is suggested to follow the proper process and take into consideration all the required prerequisites. Any error or mistake while installing the updates can stop the installation process and can also impact the server and databases.
If your Exchange Server gets compromised, you can take the help of a tool, like Stellar Repair for Exchange to recover data from the compromised server.