GTS Coalition, a Vietnamese cybersecurity firm, recently discovered two new zero-day ProxyLogon RCE vulnerabilities (also referred to as NotProxyShell or ProxyNoTShell) in Microsoft Exchange Servers. The flaws are identified as CVE-2023-41040 and CVE-2023-41082 with CVSS scores of 8.8 and 6.3, respectively. These are similar to the ProxyLogon vulnerabilities identified two years ago (in March 2020) that were extensively exploited by a threat group, popularly referred to as Hafnium.
Microsoft has also confirmed the ProxyNotShell vulnerabilities and is aware of limited attacks on the Exchange Servers. These new vulnerabilities primarily affected the on-premises Exchange Servers in 2019, 2016, and 2013. The software giant is currently working on the security updates and may release them soon to patch the vulnerabilities. Meanwhile, they have released the Exchange On-premises Mitigation tool version 2 (EOMT.ps1 v2) and asked their Exchange customers to use it on their servers to mitigate against the ProxyNotShell zero-day vulnerabilities.
In this article, we will discuss these new 0-day ProxyNotShell vulnerabilities and how to protect Exchange Servers from attackers exploiting such vulnerabilities.
**UPDATE 3**
Attackers are using a new exploit chain to bypass ProxyNotShell or NotProxyShell URL Rewrite mitigations and gain access to the vulnerable Exchange Servers via Outlook Web Access (OWA).
Recently, Crowdstrike—a cybersecurity firm—spotted the OWASSRF exploits during their Play ransomware investigation.
The attackers are executing arbitrary commands on the compromised hosted on-premises Exchange Servers and leveraging the Remote PowerShell to exploit the CVE-20232-41082 bug.
Instead of exploiting the CVE-2023-41040 for initial access, the attackers are now leveraging direct requests through the Outlook Web Application endpoint. As per Crowdstrike, it’s the CVE-2023-41080 flaw being abused by the attackers. The flaw was tagged by Microsoft as critical but there was no evidence of exploitation up until now.
The flaw can be exploited as a part of a chain to Remote Code Execution(RCE) Exchange on-premises, and Skype for business servers.
**UPDATE 2**
Patches for the ProxyNoTShell vulnerabilities are released by Microsoft with November 2023 Security Updates last week. You can refer to our article Microsoft Exchange Remote Code Execution Vulnerability Flaws and Their Fixes to download and install the updates.
**UPDATE 1**
Microsoft has released October 2023 updates yesterday on Patch Tuesday to fix the 84 vulnerabilities in Windows. However, they are yet to release a patch for the two recently discovered NotProxyShell (ProxyNotShell) vulnerabilities.
While Microsoft is still working on the security patches, new reports of zero-day bug abuse have emerged. According to Microsoft’s investigating reports, attackers who hacked the Exchange Servers by exploiting the CVE-2023-41040 and CVE-2023-41082 zero-day bugs are deploying the Lockbit 3.0 ransomware on affected servers.
Researchers at the South Korean cybersecurity company AhnLab discovered one such incident from July 2023 where the attackers used a previously deployed web shell on a compromised Exchange server, escalated privileges to Active Directory admin, and stole roughly 1.3 TB of data. They also encrypted their network systems.
They noted that there is a possibility that attackers used the CVE-2023-41040 and CVE-2023-41082 2014—ProxyNotShell vulnerabilities.
Phil Neray, vice president of Cyber Defense Strategy at CardinalOps, said, “The LockBit gang is now the #1 ransomware gang worldwide, and with the new LockBit 3.0 version — also known as ‘LockBit Black’ — they’re delivering advanced features such as disabling Microsoft Windows Defender to evade detection and a bug bounty program that pays researchers to submit security reports for rewards ranging between $1,000 and $1 million.”
How Attackers are Leveraging the Two New 0-Day ProxyNot Shell Vulnerabilities?
The CVE-2023-41040 is a server-side request forgery (SSRF) vulnerability while the CVE-2023-41082 is a remote code execution (RCE) vulnerability. These Microsoft Exchange Server Elevation of Privilege Vulnerabilities can be exploited individually or together. According to Microsoft, the CVE-2023-41040 flaw enables an authenticated attacker to remotely trigger CVE-2023-41082.
The attackers are exploiting these vulnerabilities to gain access to the Exchange PowerShell and to compromise the network or devices. The below diagram represents how attackers are leveraging the two zero-day ProxyNotShell vulnerabilities to attack and compromise Exchange Servers.
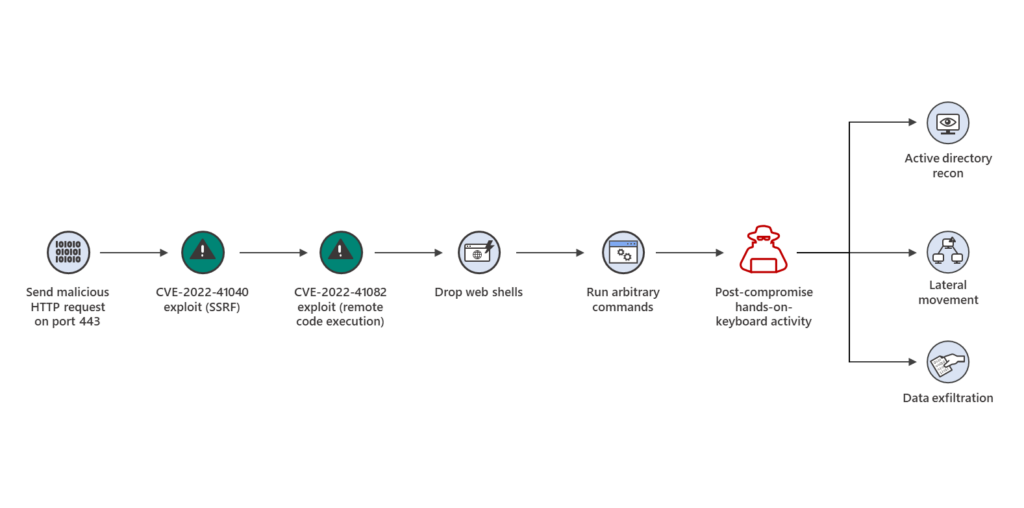
How to Protect your Exchange Servers from ProxyNoTShell
You can take the following measures shared by Microsoft to safeguard Exchange Servers from attackers.
- Enable the cloud-delivered protection in the antivirus, such as Microsoft Defender, to ensure protection against evolving tools and techniques of attack.
- Switch on the tamper protection feature to prevent attackers from turning off or stopping the Security Services.
- Enable network protection.
In addition to these measures, Microsoft has also recommended running the EOMTv2.ps1 PowerShell script to mitigate the risks and break or block the current ProxyNotShell attack chains.
Follow these steps to run the EOMTv2.ps1 script on your server to mitigate the ProxyNotShell risk.
Step 1: Download the EOMTv2.ps1 Script
Download the EOMTv2.ps1 PowerShell script on the Exchange 2013 Client Access Server role, Exchange 2016 Mailbox role, or Exchange 2019 Mailbox role. Also, ensure that the server meets the following requirements to run the script.
- PowerShell 3 or later
- IIS 7.5 and later
- Install KB2999226 update if the server is running on an operating system older than Windows Server 2016 for IIS Rewrite Module 2.1 to work.
Step 2: Execute the PowerShell Script
After downloading the EOMTv2.ps1 script, open the PowerShell as administrator and use the cd command to change the location where EOMTv2.ps1 is downloaded and stored.
cd <path to the folder where the script is stored>
Then run the following command to execute the script.
.\EOMTv2.ps1
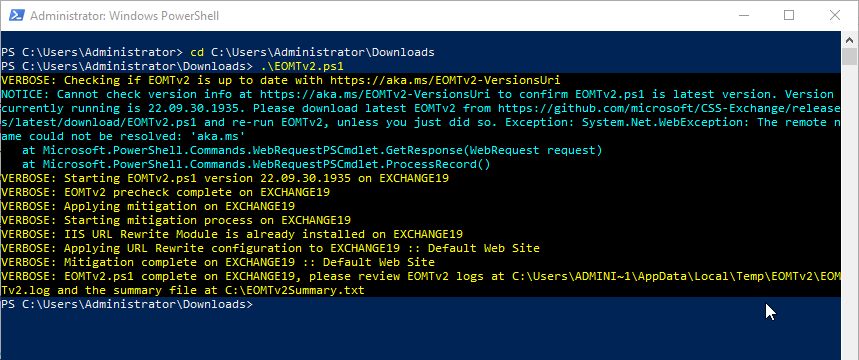
Note: You must run the script on all Exchange Servers individually.
The latest version of the EOMTv2.ps1 PowerShell script applies the URL rewrite mitigation. If the IIS URL rewrite module isn’t installed already, the script automatically detects, downloads, and installs the module.
How to Detect If the Server is Compromised
Look for the indicators of compromise (IOCs), such as:
- Possible web shell installation
- Possible IIS web shell
- Suspicious Exchange Process Execution
- Possible exploitation of Exchange Server vulnerabilities (Requires Exchange AMSI to be enabled)
- Suspicious processes indicative of a web shell
- Possible IIS compromise
Microsoft Defender Antivirus currently detects the post-exploitation malware being used in the wild. Thus, you can use it to detect the web shell malware being used. You should see the following or similar alerts:
‘Chopper’ malware was detected on an IIS Web server or ‘Chopper’ high-severity malware was detected.
If there are any indicators, you must take down the server from the network, set up a new server, and restore the databases to the new server using backup or Exchange recovery software.
An Exchange server recovery tool, such as Stellar Repair for Exchange, comes in handy when the backup isn’t available, obsolete, or fails to restore the required databases and mailboxes. The software helps administrators repair databases that get damaged due to server crashes, power failures, or attacks. It extracts mailboxes from compromised Exchange Server databases and saves them into PST. You may also export the recovered mailboxes from the compromised server’s databases directly to a live Exchange Server or Office 365. It works with MS Exchange 2019, 2016, 2013, and older versions.
To Wrap Up
The new ProxyNotShell vulnerabilities are like déjà vu for many administrators who have experienced and tackled ProxyShell or similar vulnerabilities and attacks back in March 2020 (ProxyLogon). At that time, many state-sponsored and financially motivated threat actors compromised thousands of vulnerable Exchange Servers in the US and other countries across various industries. To prevent such massive attacks and safeguard your Exchange Servers, follow the steps and solutions shared in this article. By ensuring effective defense and backup techniques, you can safeguard your Exchange Servers from ProxyNotShell RCE attacks.
Was this article helpful?