ToddyCat, an Advanced Persistent Threat (APT) gang,has been targeting and exploiting vulnerable Exchange Servers throughout Europe and Asia since December 2020. Between December 2020 and February 2021, the gang targeted and attacked a limited number of entities in Vietnam and Taiwan. The gang exclusively attacked Exchange Servers previously compromised with Samurai — an advanced passive backdoor that works on 443 and 80 ports.
They used the malware to execute arbitrary code and multiple modules to remotely administer, control, and move laterally into the targeted network. In some cases, the Samurai backdoor was also used to run another sophisticated Trojan cum loader called Ninja. They also used the China Chopper, a 4 KB web shell, to get access to the server and download and execute another dropper.
However, the ToddyCat APT gang started attacking more servers between February 2021 and May 2021. During this wave of attacks, the gang exploited the infamous ProxyLogon RCE vulnerability in the unpatched Exchange Servers. This time the gang targeted many prominent countries, including Russia, Afghanistan, India, Iran, Malaysia, Pakistan, Slovakia, Thailand, and United Kingdom.
In the next wave of attacks — until February 2023 — the ToddyCat gang increased the scope of attacks and targeted organizations in Indonesia, Kyrgyzstan, and Uzbekistan, in addition to the previously targeted countries.
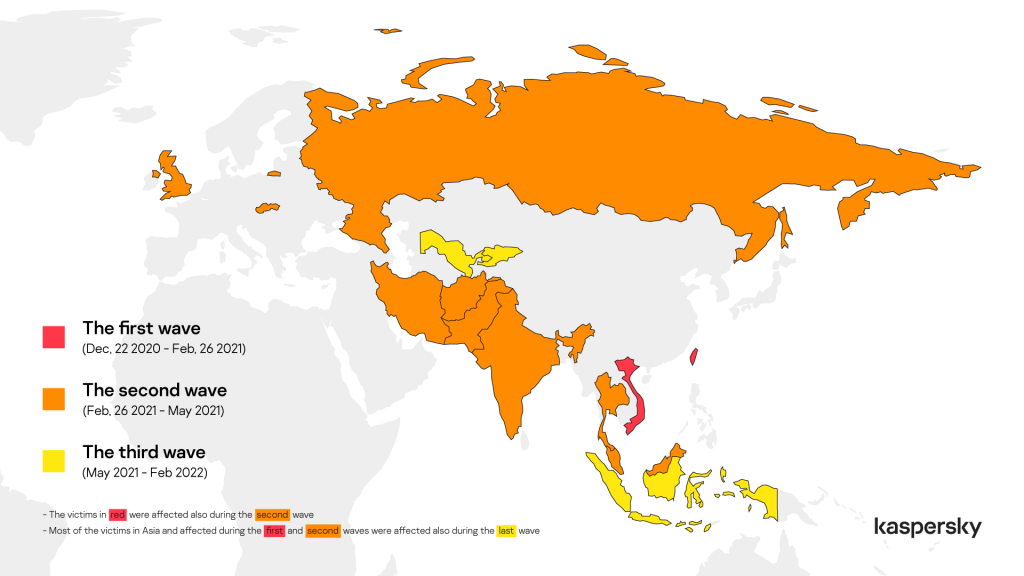 Image Source – ToddyCat attack waves (Kaspersky)
Image Source – ToddyCat attack waves (Kaspersky)How to Protect your Exchange Server Environment from ToddyCat?
To protect and safeguard your Exchange Server and network infrastructure from ToddyCat or ransomware attacks, install the latest Cumulative Updates and Security Updates on your Exchange Server to patch the vulnerabilities. Also, consider upgrading to the latest version, if your organization is using an older Exchange Server version.
In addition, follow the below steps to check your server health and detect vulnerabilities.
Step 1: Run MSERT Scan
The Microsoft Safety Scanner or MSERT tool scans servers for any malware or web shells installed on your Windows Server environment and removes them from the system. Here’s how to use it:
- Download the Microsoft Safety Scanner and then open it.
- Accept the terms and click Next > Next.
- Select the Scan type and click Next to start the scan.
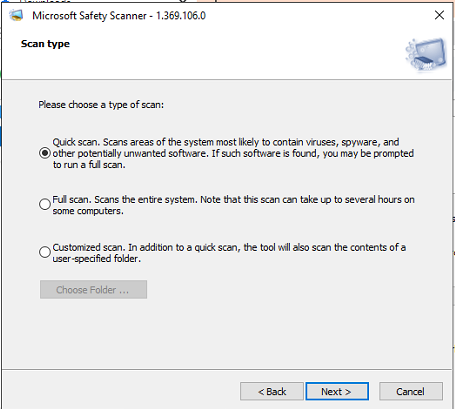
- Based on the scan type, this may take a while to complete
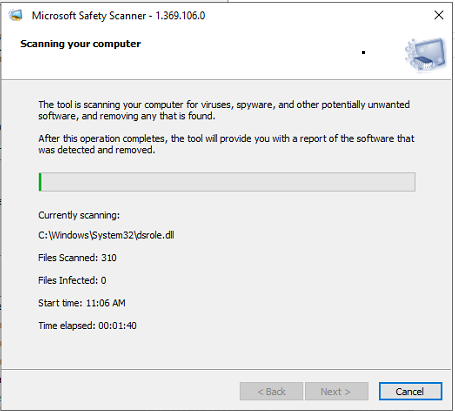
- The results are logged and stored at %SYSTEMROOT%\debug\msert.log.
Step 2: Use Health Checker PowerShell Script
You can download the HealthChecker.ps1 script from the official GitHub page and follow the steps below to execute it on your Microsoft Exchange Server 2013, 2016, or 2019. The script helps you check the server’s health, detect vulnerabilities, and patch them. Follow these steps:
- Launch the Exchange Management Shell (EMS) and run the following command. This will allow you to execute the HealthChecker.ps1 script without error.
Set-ExecutionPolicy -Scope Process -ExecutionPolicy Bypass
- Navigate to the folder location where the HealthChecker.ps1 script is located using the ‘cd’ command in the EMS. For instance,
cd C:\Users\YourUserName\Downloads\
- Then execute the following command to run the HealthChecker.ps1 script on your Microsoft Exchange Server.
.\HealthChecker.ps1 –BuildHtmlServersReport
- This will generate a detailed report in an HTML file. The file is saved in the same folder where the HealthChecker.ps1 script is located.
- Double-click on the HTML report file to open it in a web browser, such as Google Chrome or Microsoft Edge.
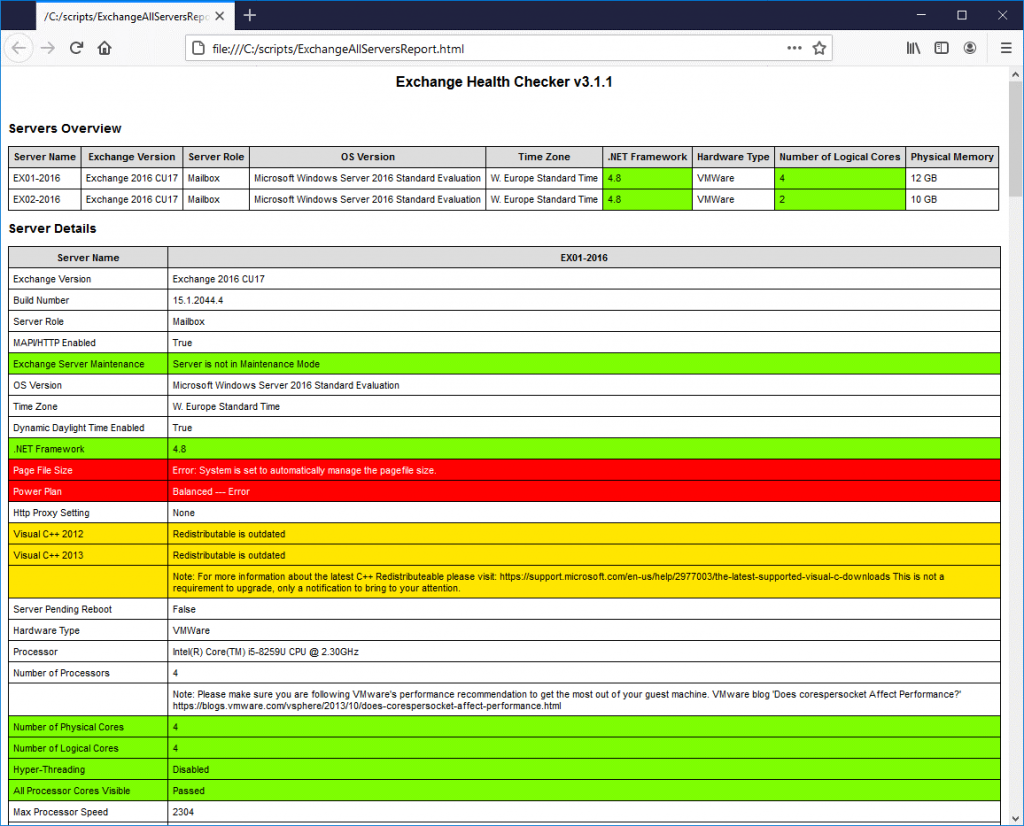
- Check and fix the issues highlighted with Red.
- In the end, check the vulnerabilities section. Then, use the links to download the updates and install them on your server.
You can follow our detailed guide to download and install the latest Exchange Server Updates.
Conclusion
ToddyCat is not a new but lesser-known APT gang that has been targeting Microsoft Exchange Servers since December 2020. It’s a sophisticated APT gang that uses various techniques to stay low profile and avoid detection. They target previously compromised or vulnerable and unpatched Microsoft Exchange Servers to steal or encrypt data for a ransom. It has affected government and private entities, including the military, mostly in Asia and Europe. The best defense against ToddyCat or ransomware groups is to install the latest Cumulative and Security Updates released by Microsoft as soon as possible. However, if your server is compromised or crashed due to ToddyCat or any other malicious attack, it is recommended that you set up a new server and restore the mailbox databases from the backup or use Exchange recovery software, such as Stellar Repair for Exchange.
Was this article helpful?