Medusa ransomware, a mobile banking Trojan targeting Android devices, has resurfaced after lying low for almost a year. Cybersecurity researchers have highlighted its resurgence in previously known country targets, like Spain and Turkey, but also new ones, such as Italy and France. As per the reports, an updated, compact version of this Trojan was introduced in May. Since then, security researchers have witnessed a massive surge in its activity. The new version seemingly requires fewer permissions to carry out transactions directly from compromised devices.
The Trojan, also called TangleBot, was first identified in 2020. It is known for its ability to log keystrokes, remotely uninstall applications and manipulate screen controls & text messages on compromised devices. The latest wave of attacks was first picked up by Cleafy, an intelligence company specializing in online fraud management.
The report claimed that the new strains of Medusa, an Android-based malware-as-a-service (MaaS) operation, are lightweight, require fewer permissions, and have advanced screen overlaying and screenshot-capturing capabilities.
Recent Surge in Mobile Banking Trojan’s Activity
Researchers claimed that Medusa ransomware variants have spiked since July 2023. Cleafy noted these variants are distributed through sophisticated phishing tactics using fake update procedures that trick users into side-loading malware on their devices via dropper applications.
They've tracked down 24 separate campaigns linked to five different botnet networks: UNKN, AFETZEDE, ANAKONDA, PEMBE, and TONY. They're focusing their attacks on several European countries, including Italy, Spain, France, and the United Kingdom. 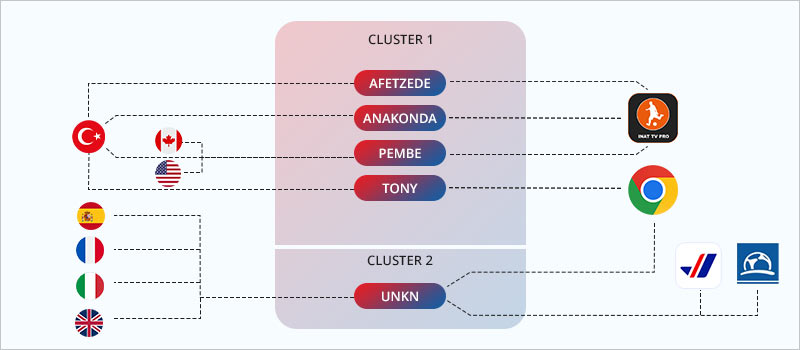
Their operations are distinct and targeted, making them a notable threat to cybersecurity. These botnets have been delivering fake dropper apps disguised as real ones, such as a 5G connectivity app, a fake Chrome browser, and even a 4K sports streaming service.
Updated Medusa Variant Released
Cleafy notes that these attacks are all connected to a central Medusa infrastructure that cleverly uses social media to spread and manage its attacks. The analysis reveals that the malware's developers have made some updates, pulling out 17 old commands from the older version and introducing five fresh ones. Here's what's new:
- destroyo can uninstall an app.
- permdrawover asks for permission to display over other apps.
- setoverlay creates a black screen disguise, which hackers use to trick you into thinking your device is off and hide malicious activities going on in the background.
- take_scr captures screenshots.
- update_sec alters a user’s confidential codes, such as passwords, key phrases
Medusa mobile banking Trojan is expanding its attack vector and setting the stage for a larger rollout, potentially affecting more people. These harmful apps have yet to pop on the Google Play store, but as more cybercriminals get in on the action, we can expect malware-as-a-service (MaaS) operations to become more prevalent and complex.
Brokewell Malware Steals User Data, Wreaks Havoc
In another news report concerning a new malware, cybersecurity researchers have uncovered an Android-based banking Trojan called Brokewell. This malware sneaks in through pathways, such as a fake Google Chrome update, and can track everything from your phone apps to messages.
The scary part? Brokewell is getting smarter, learning new ways to control your phone, and even letting hackers run it remotely. The research team at ThreatFabric, a fraud risk firm, stumbled upon Brokewell while checking out a phony Chrome update alert, a classic trick for making people download malicious software without realizing it.
The Threat Imposed by Brokewell
Brokewell is designed with some very invasive features:
- It can trick you into giving away your login details by creating fake login pages.
- Once you're logged into a site, it can collect your cookies.
- Records how you interact with your device—every tap, swipe, and text you type.
- Collects your device's hardware and software details, checks your call history, and pinpoints your location.
- Spies on you by turning on your microphone.
- Siphons user data by taking remote control of the device.
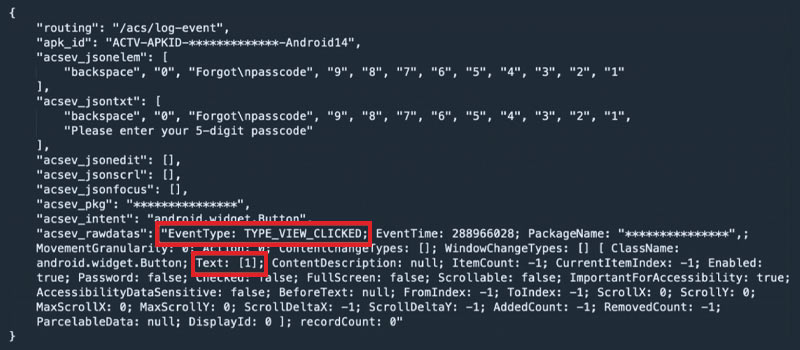
Brokewell can bypass the restrictions introduced by Google in Android 13 and later versions to curb abuse of Accessibility Services. It can push buttons on your device, provide remote access to a malicious actor, mess with your settings, and turn them down to zero.
Rafel (RAT) Malware Targets Android Users in Several Countries
In a related news report, researchers at Check Point Research found out that these threat actors are using Rafel, a Remote Administration Tool (RAT) malware to target Android users in the US, Russia, France, India, Germany, China, Indonesia, and the United Kingdom.
Hackers use sophisticated phishing techniques to spread Rafel via Telegram, WhatsApp, and Android’s SMS application. Once installed, it lurks within the device by resisting its security features.
Rafel RAT can access the host phone’s components, such as GPS, camera, microphone, and storage. This allows cybercriminals to gain confidential information about users, which is later used for blackmailing purposes or is sold to other criminals.
Concerned About Losing Data on Your Android Device Due to a Malware Attack?
Security experts are constantly raising alarms over new, advanced malware variants becoming a hot commodity for cybercriminals. Given how easy it is for a hacker to carry out fraud right from the victim's own device, this should be a grave concern for every Android user.
It is important to remember that certain Trojans will not let you create a folder or even access your device to perform recovery. In such cases, you’ll have to completely wipe out the data from your device and take it to a recovery center to regain access.
If you, too, are worried about losing data on your Android device to a malware attack, we have got you covered. Use our professional Android data recovery software – Stellar Data Recovery for Android, to retrieve all your lost or deleted data. This DIY tool supports recovery from an Android device’s internal memory without rooting it.
Stellar Data Recovery For Android
Android Data Recovery Software To Recover Lost Photos, Videos, Contacts, and More.
Simply connect your phone to a Windows PC, launch the software, and enable USB debugging on your smartphone. The software will scan and recover your lost data in just a few simple steps. But remember that the software can’t guarantee the recovery of your lost data under all circumstances. In rare cases, a Trojan may completely wipe out your data or overwrite it to the point of no recovery.
Bottom Line
Malware like Medusa and Brokewell is expected to become even more advanced with time. As part of its malware-as-a-service (MaaS) business, it plans to be distributed to more cybercriminals online. Therefore, it is better to have proper safeguard mechanisms in place.
To protect your Android device from malware attacks, avoid downloading apps from unauthorized sources outside Google's Play Store, and enable Play Protect on your device. But if you are still experiencing data loss, we highly recommend using Stellar Data Recovery for Android to retrieve all your lost data.
FAQs
Q. Why is Android prone to malware?
A. Unlike iOS, Android operating system software is open source, meaning anyone can modify it. It is easier for hackers to find and exploit security gaps if a developer makes any error.
Q. How does malware infect Android?
A. Cyber criminals send phishing emails and text messages to trick users into clicking malicious links and attachments that download malware on Android devices.
Q. How to avoid malware on Android?
A. To protect your Android devices from malware:
1. Use secure Wi-Fi networks.
2. Download apps only from trusted sources.
3. Keep your device’s OS up to date.
4. Encrypt your Android device.
5. Create a strong password.
Q. How do I know if my Android has malware?
A. Look out for the following signs of malware on Android:
1. Increased data consumption.
2. The phone and apps on it keep crashing.
3. A lot of pop-up ads.
4. Presence of unfamiliar apps on the phone.
5. The phone becomes overheated.














 5 min read
5 min read