With so much of our personal information, such as pictures, videos, passwords, and financial information, being shared online, it's vital to safeguard this information more than ever. Data Confidentiality is one of the fundamental principles that everyone should adhere to when it comes to protecting data.
Data Confidentiality refers to maintaining your data privacy and protecting it from disclosure to destructive forces or unauthorized parties, such as cybercriminals and identity thieves.
Although there are advanced technologies available to protect your devices and personal data, we still see many instances of security breaches. But sometimes, a data breach happens due to the action or inaction of the user.
Blaming technology every time for such loss won't work. It's you who has to take control and protect your confidential data!
Here, in this guide, we're sharing some best practices on building and maintaining data confidentiality to protect your personal information and devices from hackers, malware, and other threats.
How to Protect Your Confidential Data?
Protect Your Devices and Network
1. Encrypt your Device

Device encryption is a security measure that you should take to protect sensitive data from prying eyes. Encrypting your device means that data stored on your system or storage device is protected and can be accessed only by you or people you have authorized for viewing, sharing, or using this data. When you encrypt your device, it turns data in it into a secret code that appears gibberish until you decrypt the device with the encryption key or a password. So, it's the first and essential thing you should do to build data confidentiality.
2. Use "Passphrases," not just "Passwords"

We suggest using "passphrases." A passphrase is a series of random words or a sentence. You can call it a password, but it's typically long and hard and cannot be guessed by anyone. It is crucial to have a strong password comprising uppercase & lowercase letters and special characters. The more random characters in a passphrase, the stronger it is.
For example: "It was one hell of a cold afternoon, and he was waiting for her to come!" –You can convert this passphrase into an abbreviation, i.e., "Iw1hocwaahwwfhtc!" This abbreviated version of the passphrase is more extended, appears random, and difficult to guess.
3. Practice the PoLP & Multi-Factor Authentication
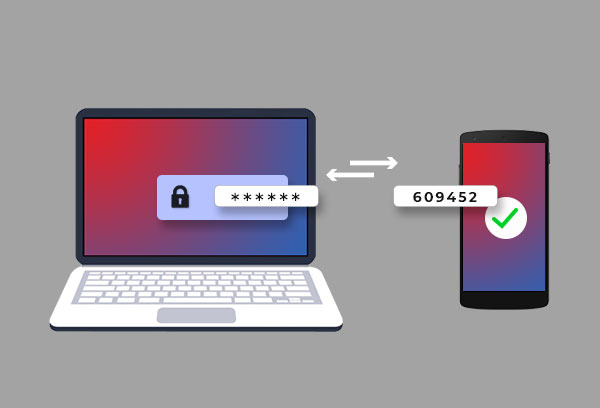
Whenever you log into your system, don't use the admin credentials/rights unless you have to perform specific tasks, such as formatting your drive, partitioning the hard drive, or creating a new user account. Running your system with administrator credentials makes your system more vulnerable to security exploits and risks. Hence, we recommend following the Principle of Least Privilege (PoLP), i.e., always use user account credentials to log in and access your system.
Along with that, enable two-factor or multi-factor authentication on your device. It's another best practice you must follow to protect your confidential data. In this method, you enter your password along with one or more authentication entries, such as your mother's maiden name, one-time password sent to your phone, fingerprints, etc.
4. Secure your Wireless Network

Whether you are a small business owner or an individual user, it's always recommended to secure your wireless with a strong password. Doing so will help you avoid any unauthorized access to your wireless network. Even if they are only trying to get free WI-FI, you won't want to share your private data with other people on your network.
Additionally, if multiple devices are connected to your home wireless network, sharing files becomes more convenient. However, making files publicly available doesn't make any sense unless necessary. Disable your media sharing if not needed.
5. Dispose of Your Devices Securely

If you do not wish to keep the data in your device or if you wish to dispose of the device altogether, then it's important that you securely and permanently erase the data in it. A permanent erasure and not ordinary deletion via formatting or Recycle Bin/Trash can accomplish that. Let's look at this subject in detail below.
If you wish to dispose of, sell, or donate your device to someone, and the data stored on the device is no longer required, ensure that all the data is erased permanently. Don't just delete or format the data, but perform a permanent data erasure. To permanently erase the data beyond recovery, you can use reliable data erasure software.
Formatting the drives or putting the files in Recycle Bin in Windows (Trash in Mac) and then emptying the Recycle Bin doesn't wipe them permanently. The system makes the space free to store new data. However, the files remain available on the system in an inaccessible state unless overwritten. Anybody can use data recovery software to recover that inaccessible data. Therefore, it's crucial you permanently delete your confidential data beyond recovery to prevent a data breach, identity theft, or any other threat.
Protect Your Data and Identity Online
6. Don't Open Emails from Suspicious Senders

Emails are beneficial, but at the same time, an easy target for hackers. The majority of cyberattacks start with a single phishing email. So, if you know how to spot a phishing email, you can avoid a phishing attack, data breach, and several other threats. The first step you can do to protect your data and identity online is not to open the email from individuals you don't know or recognize.
Spam emails usually come with an attachment or consist of some link that may contain malware or virus. If you receive an email from an unknown source with a file or link, don't download/open the files attached with it. Simply delete the email from an unknown or suspicious source to avoid damaging your device and data.
7. Don't Save Passwords in your Browser
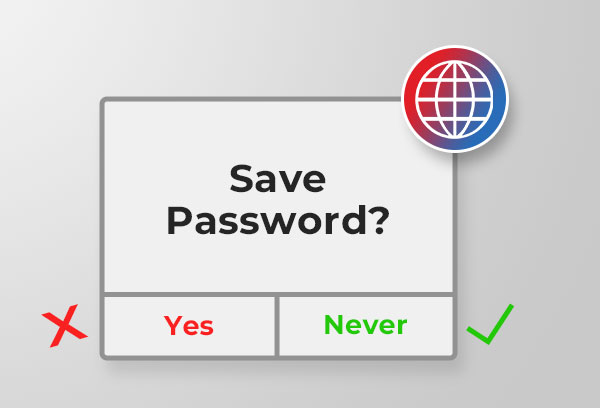
Avoid saving your login credentials in any browser. When you log into your browser, you might want to leverage the 'remember password' feature available in browsers like Chrome, Internet Explorer, etc. This feature auto-fills the password section whenever you want to log in to a particular site for which you have saved the credentials. It's convenient as you don't have to remember and enter your password every time you access that website.
However, it may turn out to be dangerous if someone with malicious intentions gets access to your system; they'd be able to access all your accounts for which you've saved login credentials in the browser. So, it's better to keep an eye on such pop-ups and deny them every time to ensure data protection.
| Also Read:How Can I Erase All My Browsing History at Once? |
8. Beware of Impersonators

Many impostors try to trick unsuspecting users into providing their details, such as credit card number, OTP, etc., by pretending to be an individual from their bank, credit card, or sim card company. It can happen online via phishing emails, sites, or over the phone. Hence, the best thing to do is always use caller ID and spam blocking apps on your phone to avoid picking up any spam calls.
Even if you receive a questionable call, providing you offers, discounts, asking to pay your bills, or your account details, don't give away any information and hang up immediately. Additionally, if you receive an email from a company that claims to have an account with you and asks you to share confidential data with them, don't click on the link. You can type the company's name into a web browser, go to their site, and contact them via customer service to cross-check the email source's authenticity.
9. Never Use the Same Password for All Accounts
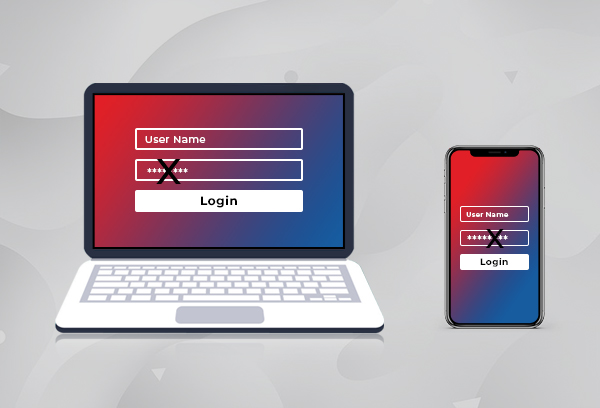
If you're using a single password for all your accounts and services, stop doing that immediately. Using the same password for every site/account is like putting all your eggs in one basket. If the hackers crack your password, they'll have the key to access all the websites and information they may use to harm you.
We understand that remembering a different password for every site/account is problematic. But it's also essential to make it impossible for hackers to get to your personal information/accounts. You may enable multi-factor authentication and use passphrases instead of passwords, as suggested above. It'll help you boost your data confidentiality.
10. Say 'No' to Share Account Details over Public WI-FI Networks

Never use a public WI-FI to share your account passwords. Data on your device shared over a public or unsecured network goes out in the clear text, and anybody else using the same network can easily access that data with just a few simple software tools. Using the public/unsecured network puts you at risk of hijacking.
Hackers monitoring the Wi-Fi traffic can attempt to take over an open session and steal the browser cookies, services that can identify you. If you use one password for multiple sites and hackers get successful in picking up your password, they can use this to steal your identity, compromise your accounts, or even commit fraud in your name.
How to Protect Yourself on Social Media
11. Don't Share Everything on Social Media

Social media information leak is undoubtedly the primary concern for millennials when they are already preoccupied with wondering what to post, when and where to post, and how many times. Worry not; there are some universal points you need to consider to protect your data on social media platforms.
- Don't share your travel itinerary (trip location, travel route, accommodation details, etc.) on social media platforms until after you return.
- Disable your geolocation on social media. There's no need to share your location with everyone who sees your posts.
- Avoid sharing information such as your date of birth, address, ID card details used to verify your identity.
- Keep an eye on all the 'Fun quizzes' asking your details such as where you went to the school, your nickname, etc. Don't share such data while playing any fun quizzes.
- Don't share the screenshots of your personal chats in social media inboxes. Even if you don't want to, you may inadvertently share some personal information about you or your friend through these screenshots.
12. Customize your Privacy Settings

Social media sites, such as Google, Facebook, and Instagram track our keywords, likes/dislikes, and what we follow on these platforms. Your social media platforms get to know you on a deeper level based on this information. Hence, customizing your privacy becomes vital.
Social media platforms, be it Facebook, Instagram, LinkedIn, and Twitter, let you customize their privacy settings. You can use their 'Privacy' settings and always choose the highest level of privacy to make sure your confidential data, such as your place of employment, hometown, date of birth, etc., are only visible to trusted people.
The content you post on social networking sites will be around until you delete them. You can customize the privacy settings. Being selective while sharing your details may affect who can contact you and see the content you post. However, keeping your online reputation in mind can be highly beneficial for you.
13. Not Everybody is your "FRIEND"

There may be times when you receive friend requests from people that you don't know. Whenever it happens, don't just start accepting friend requests from random people. Know your overall aim. Like LinkedIn's purpose is building professional networks among colleagues, contacts, hiring managers, and clients. Do your research and beware of fake profiles.
Before accepting anybody's friend request, do a quick Google search about such people for their name and pictures to ensure it's the same person. Also, use tools to manage details you share with your friends in different groups or even have multiple pages.
If you are a blogger or influencer, create a page to encourage broad participation and limit personal details. Use your profile to keep only real friends and family members.
14. Protect your Tweets

Twitter is a great platform to interact with a niche audience and connect anyone in the world. However, over the years, it's been criticized for being a place full of abuse and harassment. So many people have been targeted for threats, spamming, account hacking, and more. It's understandable that if you're using Twitter to promote your business, you may want your tweets to be available to everyone. But if you use it for personal use, keep your tweets private and share them with only your followers.
Additionally, follow the below-mentioned practices to stay safe on Twitter:
- Broadcasting your live location online is not advisable. Disable your tweet location.
- Control your photo tagging on Twitter to avoid getting attacked by spammers.
- Control the advertising and data tracking by turning off personalized ads, identity, location, and other details.
- Block suspicious accounts and hide tweets with sensitive material you don't want to make public.
- Provide your reasons and report the accounts you find abusive to protect your online reputation and data.
15. Block Suspicious Users
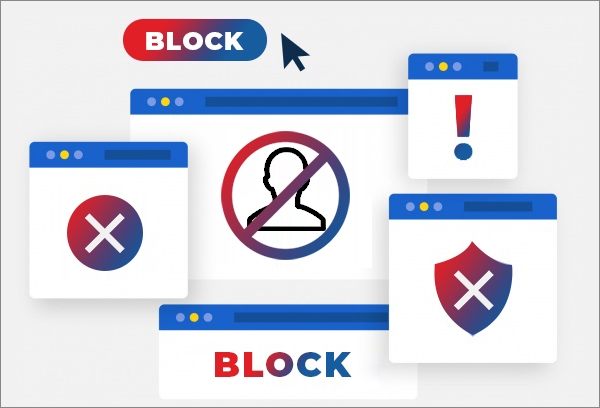
All social media sites such as Facebook, Instagram, WhatsApp, LinkedIn, etc., give you the power to block all the people/accounts that bother you. If you find any accounts suspicious, you can block them right away. Blocking people will allow you to stay safe from harmful elements. When you block someone, they become unable to access any of your data shared online. They can't message you, see your pictures, contact you, or see that you're active at all.
Best Practices to Prevent Data Breach
Data Breach may occur due to multiple reasons, such as hackers gaining access to the data or device with unencrypted data. You can protect yourself against data breach by following the best practices given below:
16. Keep Antivirus Program updated

Antiviruses and Firewalls are shields that are designed to protect your computer from online hackers. You must use antivirus software to protect your device from any virus that can crash your device, destroy your data, or even allow hackers to send email through your account. Such software scans your system, files, apps, programs, and incoming emails for malware and deletes anything that seems malicious.
Hence, keeping your antivirus program updated is a must to cope with the latest 'bugs' circulating the Internet. Ensure that the program continuously runs and checks your system for viruses, especially if you're using downloaded software or any file from the web. Don't forget to give your system a thorough scan at least twice a month.
17. Monitor Data Leakage

Track the motion of your data within your home network. It will help you avoid any unintentional use of sensitive data and protect you from potential online threats. Additionally, monitor the traffic on all networks. Usually, hackers thoroughly inspect a network for six months before breaching it. You can prevent this from happening by identifying unusual behavior. Also, periodically check the security controls; it will help you locate any private data available for public viewing.
18. Erase Data You No Longer Need

Always keep your laptops/computers, mobile devices, and storage devices clean from any sensitive data such as chats, pictures, videos, etc. Keep the data you need for routine work and safely destroy the older data from your devices. However, simply deleting your data from your devices will not help you remove them permanently. You need to wipe the data beyond recovery to protect it from malicious sources.
Final Words
We've covered the best practices that you must follow to protect your confidential data. These practices ensure that your data doesn't fall into unauthorized hands. And, if you want to dispose of, sell or donate your device or delete confidential data permanently, don't forget to use a powerful data erasure tool, such as Stellar File Eraser. You can use this DIY file eraser software that erases your confidential or sensitive data beyond the scope of recovery, thereby protecting data from falling into the wrong hands.










 6 min read
6 min read





